Malware Campaign Targets Banking Institutions
Blog
Thought Leadership
Malware Campaign Targets Banking Institutions
Troy Gill

 This morning we observed a new malware campaign that appears to be exclusively targeting banking institutions with a malicious PDF.
This morning we observed a new malware campaign that appears to be exclusively targeting banking institutions with a malicious PDF.
This comes at the same time the FBI is warning of an impending choreographed “ATM cash-out” that, in the past, has netted cybercriminals millions. Part of this attack requires cybercriminals to gain access to banks or payment processors so that they can lift ATM card cash withdrawal restrictions prior to their coordinated withdrawal.
The messages claim to contain a “Payment Notification” from Capitec Bank. In reality the messages are coming from what appear to be botnet nodes all over the world. After further investigation, we found that every recipient of these messages were, in fact, banks or financial institutions.
With this highly evasive malware being sent in such a targeted fashion, it begs the question — could these activities be related?
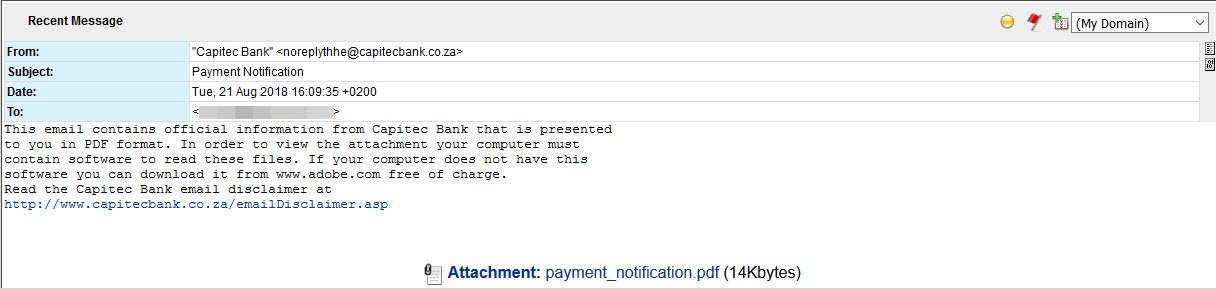
The PDF file attached to these messages functions essentially as a downloader which pulls down a Spyware infection to the target. The PDF calls a PUB file which contains A VBA macro which launches the infection chain.
Seen here:

This malware goes to work taking an inventory of the now compromised target system. It disables error messages and security warnings to hide its activity and not arouse suspicion. It also loads code which performs a browser hijack. Browser Hijacking is often used to generate advertising revenue but are also frequently used to steal banking credentials as well, which seems more likely the case here.
As of Tuesday morning, AppRiver had quarantined several thousand of these types of message.
