Email Bombs Disguise Fraud - Distributed Spam Distraction
Blog
Thought Leadership
Email Bombs Disguise Fraud - Distributed Spam Distraction
David Pickett


Email Bombs Continue to Disguise Fraud
Email bombs are a type of Denial of Service (DoS) attack. Victims face an uncontrollable deluge of messages quickly filling up their inbox when the attack begins. With enough volume, the attack renders the victims mailbox useless. Victims struggle to make sense why a sudden avalanche of messages are filling up their inbox, however, this is no accident.
Motives for the attack vary but the vast majority we see are to perpetrate some type of fraudulent activity with the victims compromised information. The bomb is typically designed to distract the user from emails generated due to fraudulent purchases or financial account updates or transactions. During these type of attacks, we've observed fraudulent airline ticket purchases, Apple store orders, and quite a few Best Buy pickup orders. If applicable to the fraudulent purchase - such as a Best Buy pickup order, attackers have mules ready to quickly pick up the fraudulently purchased merchandise soon after the attack begins.
If you or someone you know is being attacked: Victims should immediately begin monitoring financial accounts for any suspicious activity. If the victim is an AppRiver customer, contact us for assistance in mitigating the attack. We are the only email provider who has the capability of turning on a proprietary Email Bomb / Distributed Spam Distraction (DSD) protection filter. This will vastly reduce the inbound surge of emails to keep the mailbox usable during the primary attack. Attackers have even attempted to contact us surreptitiously to try find out how we do this.
HOW email bomb ATTACKS WORK
Weak Website Newsletter & Form Sign-Up Verification
While email bombing attack methods vary, most attacks we observe use legitimate newsletter sign-ups from normal websites. The email bombers utilize automated bots which crawl the web searching for newsletter sign-up pages or forms that don’t require a form of live-user authentication.
Attackers maintain lists of these vulnerable sites, some will even advertise how often they update their attack lists. Once the email bomb order is placed, scheduled, and begins - the bots will sign an unlucky recipient up for all these newsletters all at once. This generates thousands of emails arriving to the victim immediately. Beside the immediate impact, victims receive an annoying steady flow of unwanted emails that will keep arriving years after the initial attack. To add further frustration, the victim is added to additional spam, phishing, and malware lists by malicious actors. Since the bombs originate from numerous sources, this is a Distributed Denial of Service attack (DDoS).
Dark Web Attacks for Hire
Unfortunately there are many sellers and marketplaces on the Dark Web catering to anyone wishing to email bomb someone. The number of sellers on Dark Web markets have increased since we began tracking the different email bombers. These sellers will request the email address and desired starting time for the email bomb.
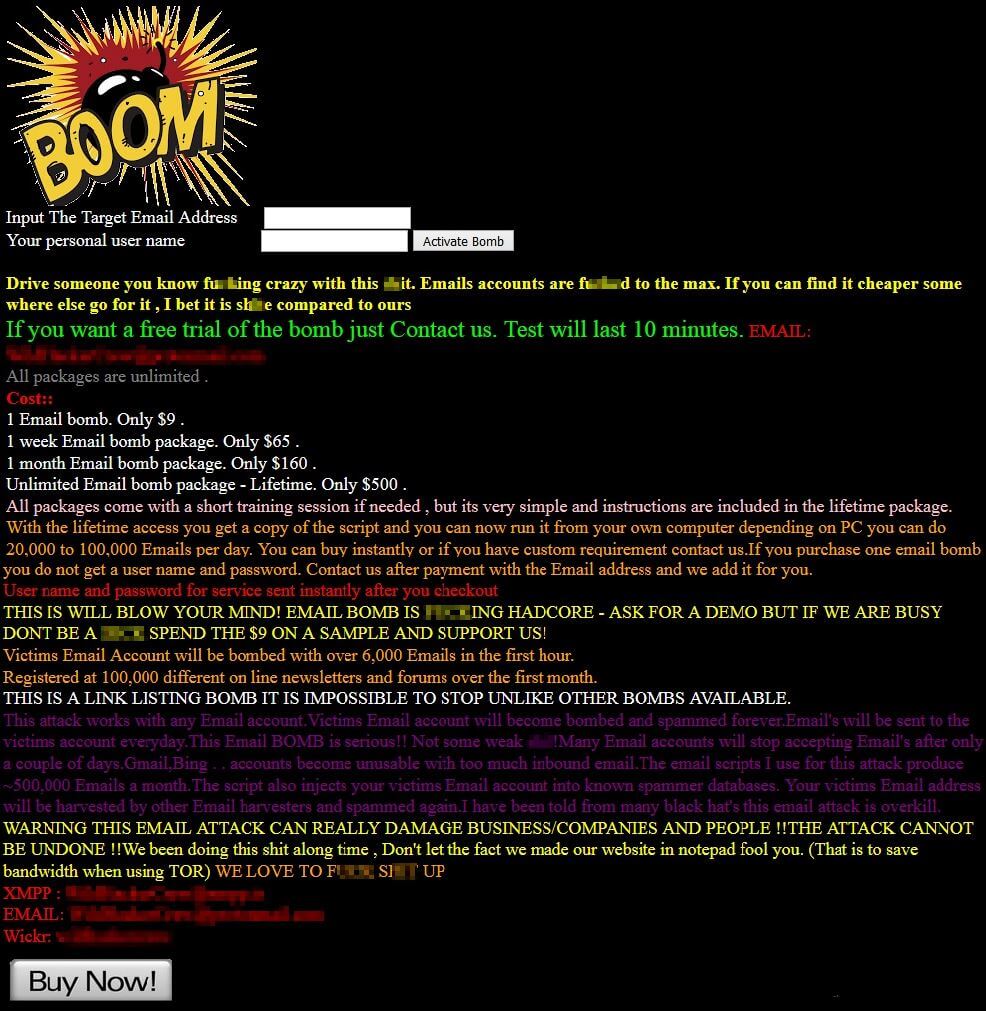
Pricing structures vary for email bombs, however, one of the most “reputable” sellers who has been around the longest charges approximately $15 per 5,000 messages. Like any enterprising model they offer price breaks for higher quantities - $30 for 20,000 messages and so on. Below is a sample advertisement posted by a hacking group that we pulled from the Dark Web. This group's bomb is based on length of time instead of quantity of messages sent.
To ensure your mailbox can withstand an email bomb contact us today for a free trial of our Advanced Email Security.