Malicious Actors Are Buying Us Flight Tickets??
Blog
Thought Leadership
Malicious Actors Are Buying Us Flight Tickets??
Chris Lee

Of course malicious actors aren't out there buying flight tickets for us, but hey I got you to click right?
Very recently we've seen a resurgence of flight ticket confirmation emails that at first glance look quite convincing (Shown below), it must be an effective tactic as it doesn't seem to go away for long. I'll also note that we saw a 100% capture rate with these recent attempts.
You'll notice in the example below that the malicious actors randomly generate a "ticket confirmation number" and a number of other details in order to lure their victims. Additionally there's nothing in the "To:" field meaning the recipient has been BCC'd (Blind Carbon Copied) on the email which we see bad actors doing a lot of lately, I wrote in depth about that here.
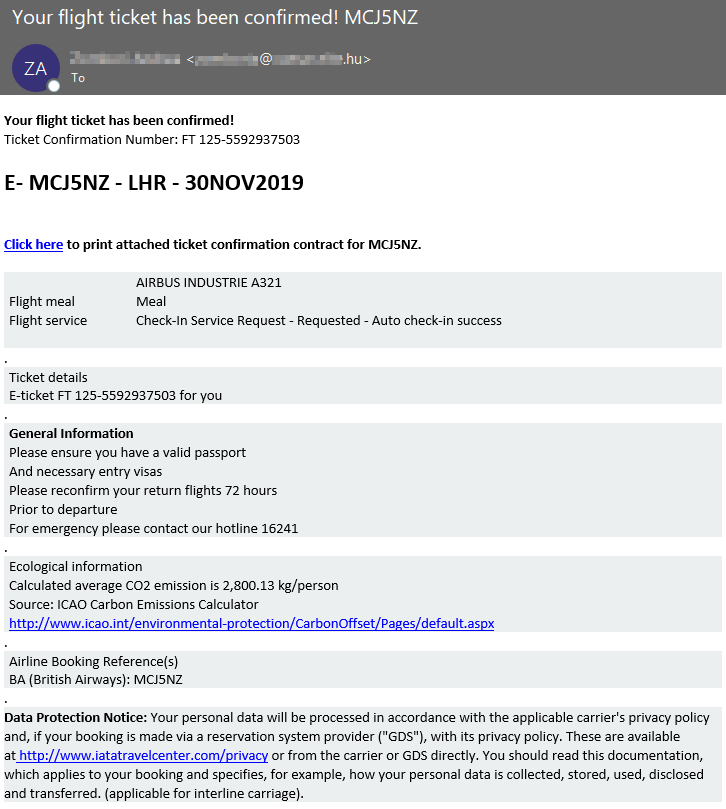
Common sense goes a long way when presented with an email like this, if you or anyone else with access to your payment/banking information didn't buy a flight ticket, you can obviously dismiss this immediately.
However if they did succeed and peaked the interest of a recipient and got them to follow the "Click here" link, they will be in for a bad time.
In this case the malicious actors are linking to a service called SendSpace which is frequently abused because it provides free large file hosting and sharing.
As soon as the link is clicked the site is loaded and a file is downloaded immediately called "Flight Ticket Confirmation PNR-TW7TW.iso" (Shown below).
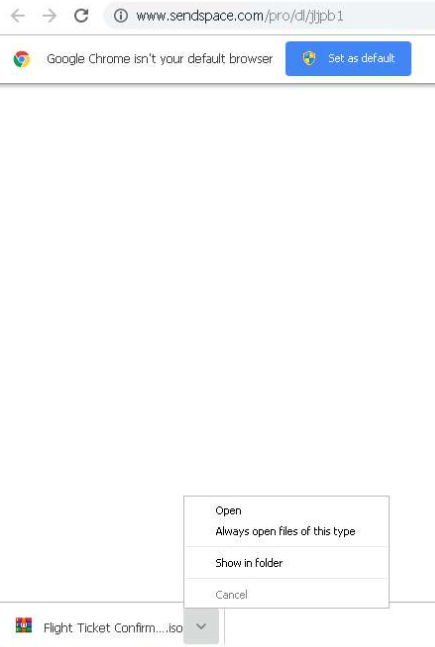
This is an immediate and in your face red flag because .iso files are used for distributing large files that are intended to burned to an optical disc (i.e. CD/DVD), this definitely isn't something you'll see when looking for your flight confirmation details.
If the .iso file is extracted and run then you'll be infected with AgentTesla which is a fully customizable password & info-stealer offered as malware-as-a-service.
Malware-as-a-service is when a threat group grants access to their hardware and software for payment. These threat groups have different payment models and 24/7 support in a lot of cases and makes it extremely easy to get very dangerous malware in the hands of a lot of people with ill intent. Because it's a malware-as-a-service model we're seeing AgentTesla being distributed with a myriad of tactics, this just being their latest one.
