SPISHING Attacks: Phishing Emails That Talk
Blog
Thought Leadership
SPISHING Attacks: Phishing Emails That Talk
David Pickett

A New Twist
As a company who protects 60,000+ businesses worldwide, AppRiver's Security Team has no shortage of phishing emails to continuously defend against. While analyzing samples for new techniques and tactics we ran across one that was a familiar phishing scam with a surprising, but amusing twist.
This one, while very simple, was different in its own unique way in the fact it actually spoke to us. Text-to-speech conversion isn't anything new in the computing world. However, it was the first time we had "heard" it tied to a phishing email.
Below, we will detail this simple, yet effective, attack we're going to call "SPISHING" and touch on brief implications it holds for future Artificial Intelligence driven natural language processing attacks.
The message below is very simple, which contributes to its effectiveness.
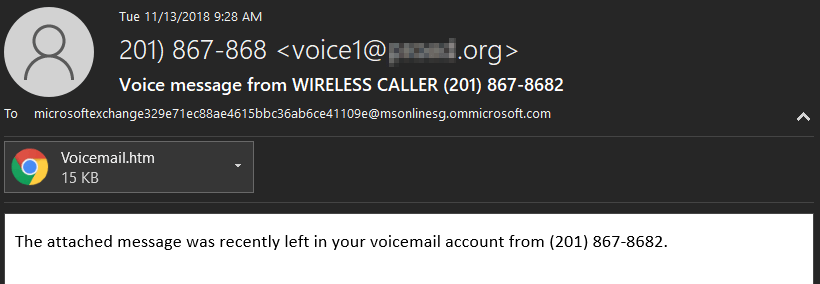
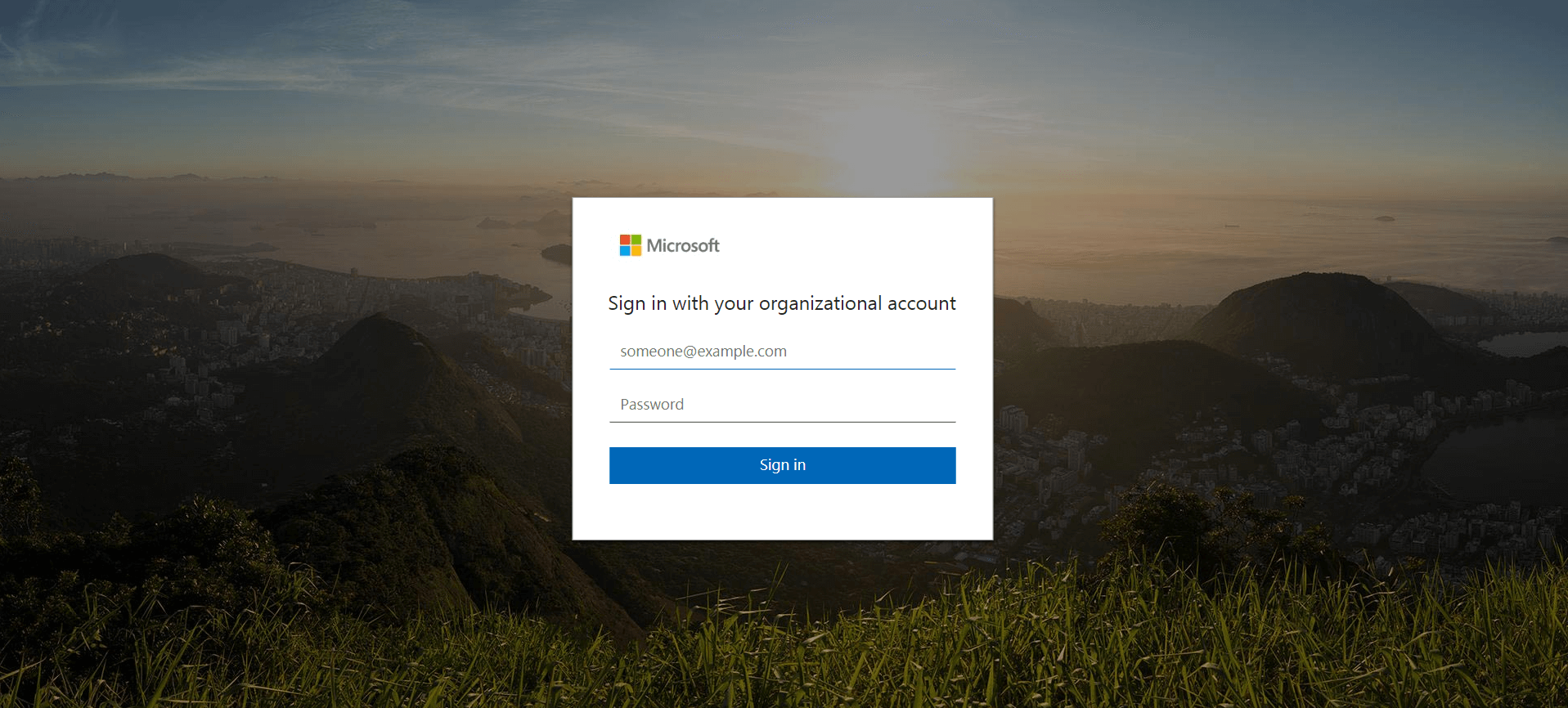
Upon opening the attachment a user is looking at a Microsoft login screen and the Spishing message begins to play thru the computer's audio. It says, "Welcome to your voicemail! Login to your account to access this message!"
Upon viewing the source code below, there is a very simple Javascript section at the beginning that utilizes the browser SpeechSynthesis API.
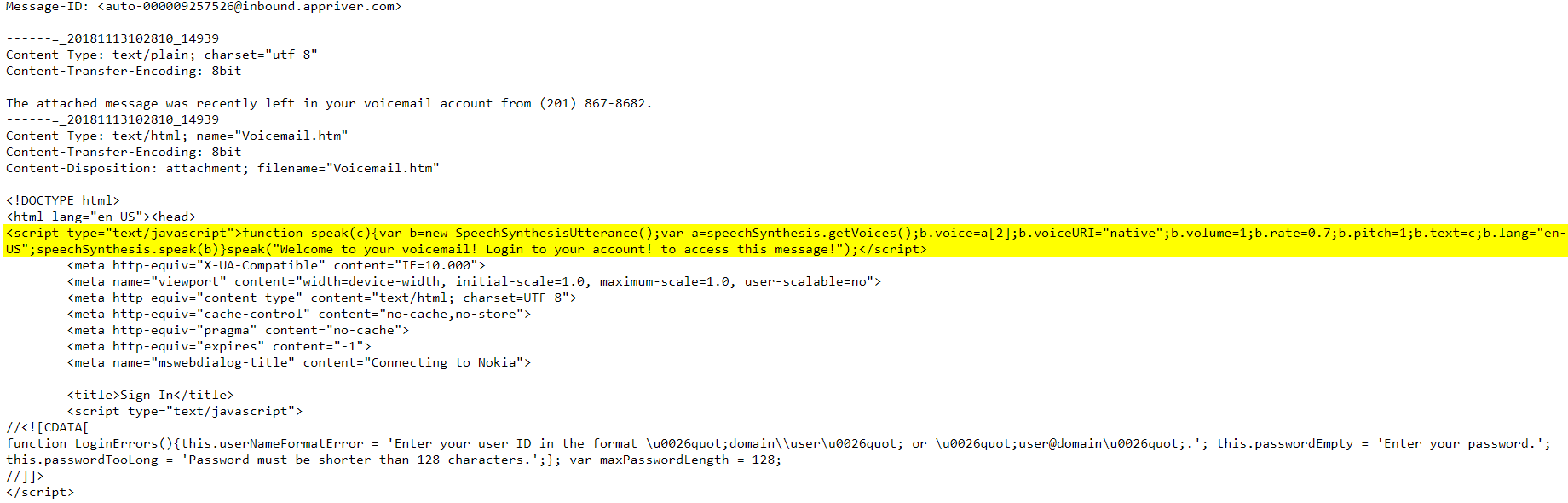
More information on the SpeechSynthesis API can be found at Google's or Firefox's development sites. Microsoft also offers a very fun browser demo tool that provides endless entertainment with a variety of voices and languages. Last week "lucky" random staff members who visited our security team's area at certain times were greeted with select phrases.
Different Types of Phishing Attacks
Vishing - Voice Phishing via a live person, utilizes cellular or landline phones Smishing - SMS/Text Message Phishing Spishing - SpeechSynthesis or text-to-speech software thru device audioImplications for Artificial Intelligence driven Speech Attacks
Attackers have weaponized machine learning and AI-driven phishing attacks. We are quickly entering an era where it will be possible for previously recorded voices to be used to drive these types of attacks, especially in BEC (Business Email Compromise) attacks.
Imagine receiving an email from a supervisor or business associate with a voice message containing instructions (for the malicious actors purpose) in their own voice, grammar, style of speaking using AI-driven natural language processing. It will be possible for attackers to use anyone's voice (dead or alive) for an attack.
APPRIVER PROTECTIONThere is no shortage of spam, malware, phishing or nefarious websites AppRiver's staff and systems continuously protect and defend against. Malicious actors work around the clock to infect your network, and we at AppRiver work even harder to stay one step ahead of them. Our team is here 24/7 365 days a year protecting and supporting clients from Office 365 Business Email Compromise Attacks and other security risks.
We always recommend defense in depth by utilizing layered security solutions. Adding SecureTide email filtering for inbound/outbound email traffic and SecureSurf for web filtering in conjunction with the built-in offerings of Office 365 or Microsoft 365 is an example of this. This builds upon the existing security functionality integrated into products and provides a more comprehensive security solution that will greatly enhance protection for users.
