Phishers Are Targeting Your Calendar With .ics Files
Blog
Phishers Are Targeting Your Calendar With .ics Files
Chris Lee

Phishers are continuing to use one of their lesser known tactics, phishing through .ics (Internet Calendaring and Scheduling Core Object Specification) files. In today's campaign these .ics files contained a link that eventually leads you to a Wells Fargo branded phishing page.
Lets dive in, here's the email in question:
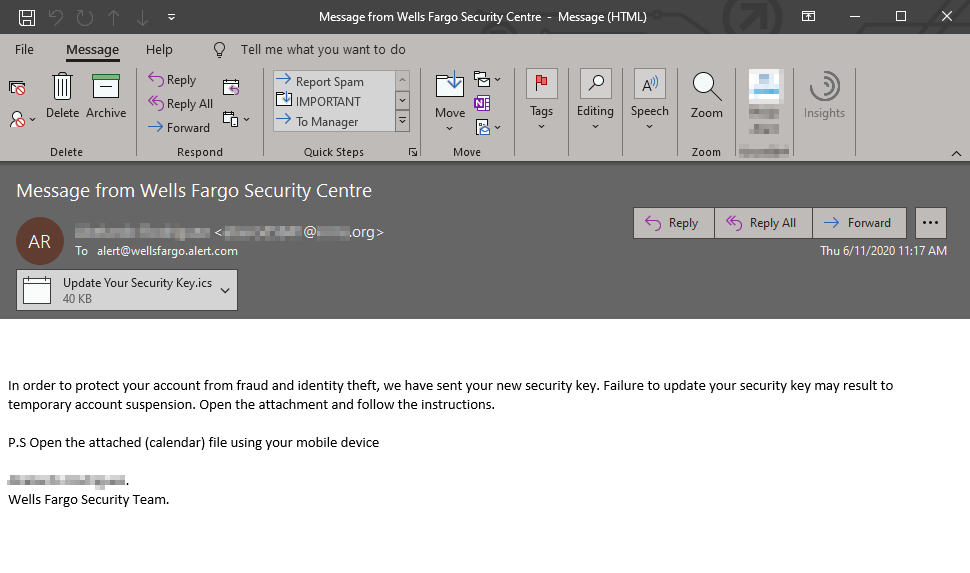
The typical sense of urgency can be seen here where they threaten to suspend your account, a very common phishing tactic. Additionally they're urging you to open the .ics on your mobile device which is a red flag, this is likely an attempt to avoid business security solutions from picking up on it. Lastly they're addressing this email to "alert@wellsfargo.alert.com" to give the appearance of some legitimacy and they're actually BCC'ing (Blind Carbon Copying) their targets. BCC functionality is being utilized in a large amount of phishing activity nowadays, I wrote in depth about this last year, that blog can be found here.
Opening the .ics file will automatically launch your default calendar application and load up the calendar appointment:
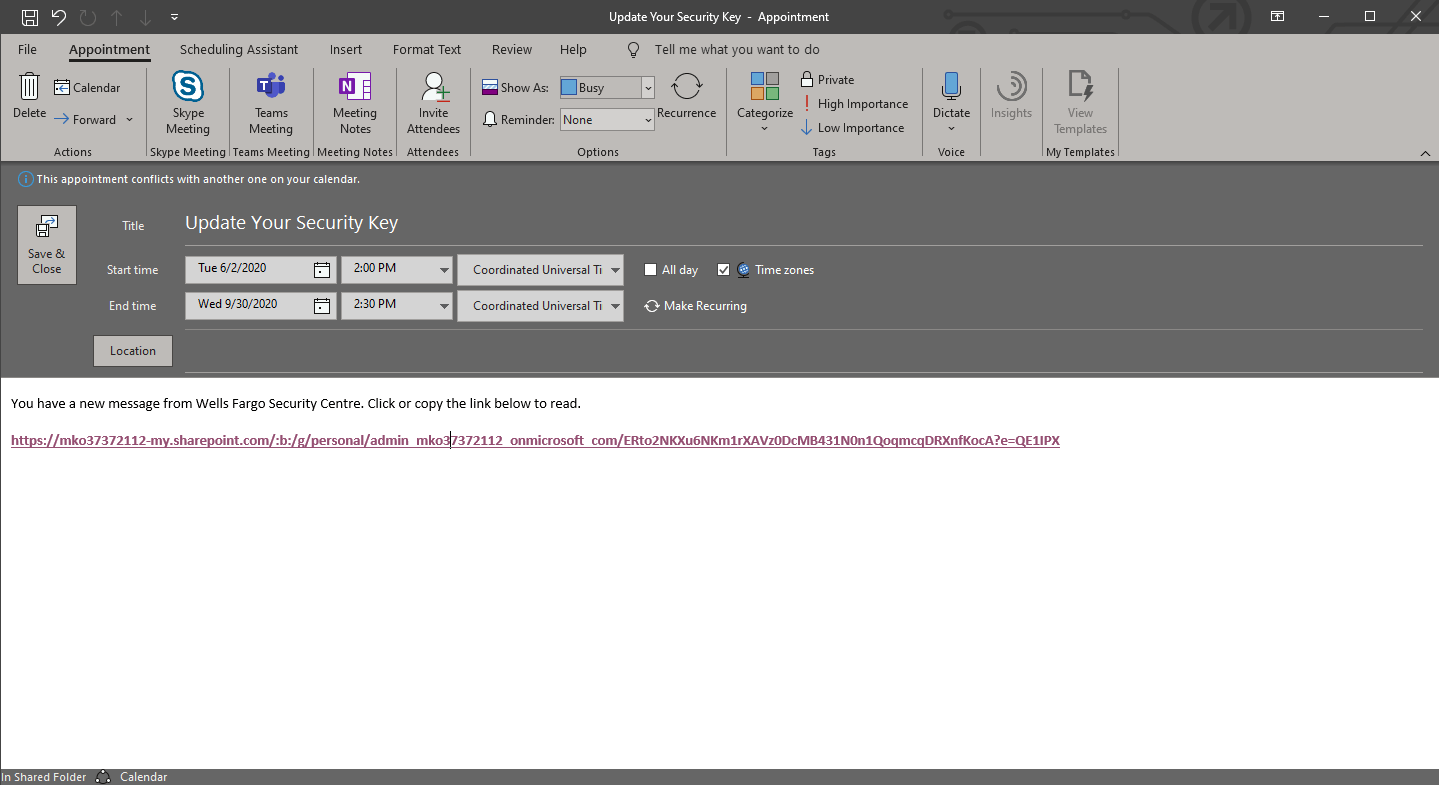
Sanitized URL: https://mko37372112-my.sharepoint[.]com/:b:/g/personal/admin_mko37372112_onmicrosoft_com/ERto2NKXu6NKm1rXAVz0DcMB431N0n1QoqmcqDRXnfKocA?e=QE1IPX
In this campaign the phishers lure you in with an unsuspecting OneDrive link, this is what is referred to as "Living off the land" phishing.
Living off the land attacks can be used for both malware the and phishing campaigns. The list of legitimate services abused for these attacks is endless, but some of the common ones include Microsoft Azure, Forms, Sway, SharePoint, Onedrive, GoogleAPIs, SendGrid, WeTransfer, SurveryGizmo, Firebase and Dropbox.
In addition, attackers prefer to launch attacks abusing these platforms from previously compromised accounts that were previously compromised. This way the sender’s IP and legitimate originating infrastructure raises less suspicion to email filters and receiving users. Attackers will often preserve the compromised users' signature and images, such as company logos, normally sent in the users' emails.
Clicking the OneDrive link takes you to this image being hosted in the senders OneDrive account:
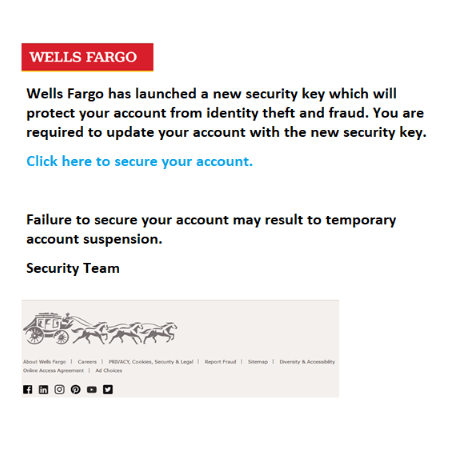
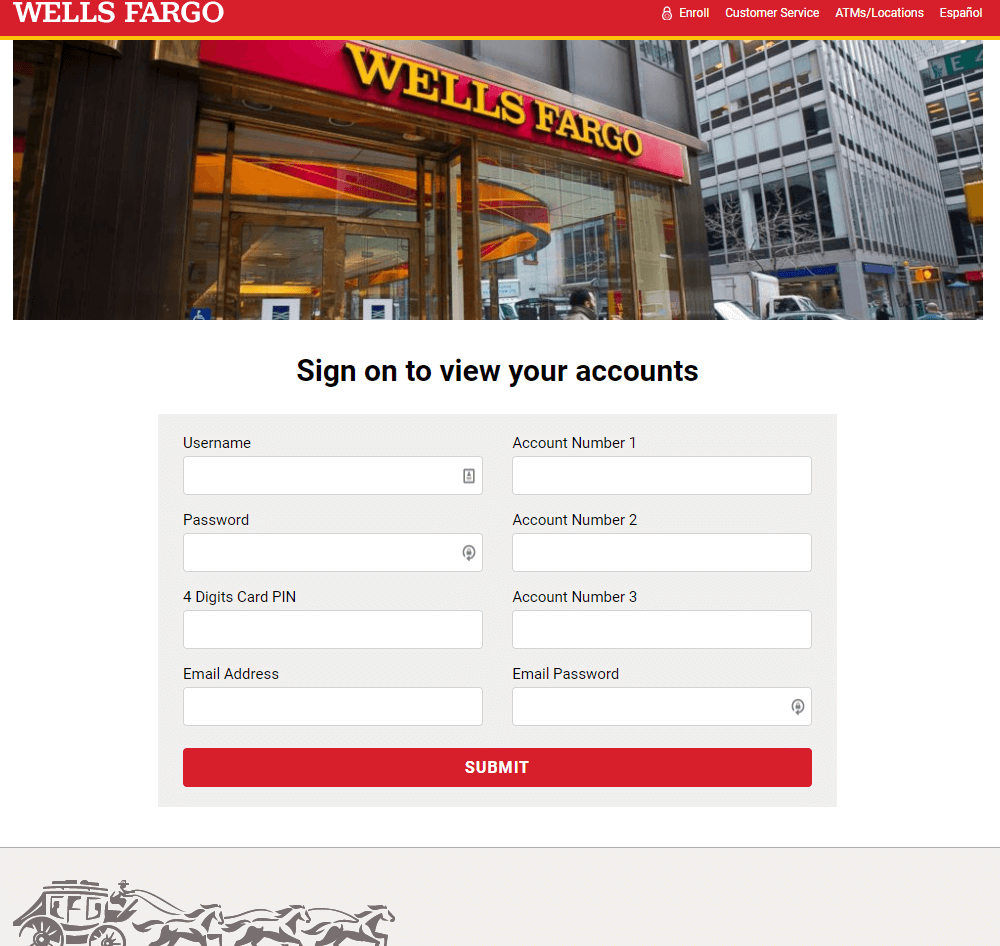
The image above links to a Wells Fargo branded phishing page that is hosted on storage.googleapis.com (Shown below). You'll notice these phishers are harvesting as much information as possible, including multiple account numbers and card PIN number as well as email address and password.
Sanitized URL: https://storage.googleapis[.]com/awells-frate-344200259/index.html
In summary, please remain vigilant when receiving a calendar file, especially from unknown senders. If you have an inkling that it may not be legitimate, please reach out to your IT/Helpdesk team prior to interacting with said file.
We observed a 100% capture rate for this campaign today.
Contact us today for a free trial of our Advanced Email Security
