Threat Actor Targeting CPAs by Posing as Doctor Seeking Tax Services
Blog
Threat Actor Targeting CPAs by Posing as Doctor Seeking Tax Services
David Bisson

A threat actor is targeting Certified Public Accountant (CPA) firms by posing as a doctor who’s in need of professional tax services.
Searching Through Generic Tax-Related Scams
Troy Gill, manager of security research and senior security analyst for Zix | AppRiver, came across the attack on February 15.
At the time, he was digging through some run-of-the-mill tax scams in which the malicious actor had impersonated the U.S. Internal Revenue Service (IRS).
Take the ruse shown below as an example.
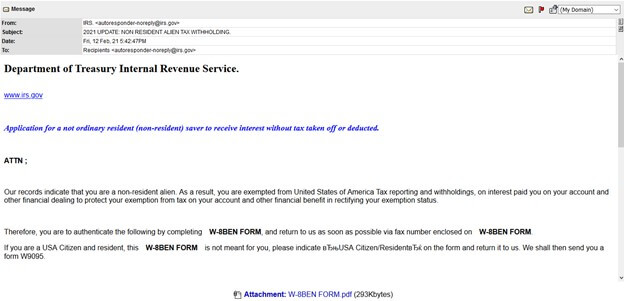
Using the subject line “2021 UPDATE: NON RESIDENT ALIEN TAX WITHOLDING.,” the email informed the resident that they were exempt from U.S. tax withholding and reporting because of their alleged status as a non-resident alien. The message went on to instruct the recipient to confirm this fact by filling out an attached W-8BEN form.
The purpose? Gill laid it out:
This is looking to gather personal and bank details which would be sent back to the attacker by fax…. These are common, and this template is nearly identical to ones we have seen used in years past.
One Attack Instance of Note
In the process of his investigation, Gill came across a scam that was a bit more interesting.
The attack email arrived from Russia with the subject line “Request for Tax Preparation from Dr Kim!!” Those responsible for launching the phishing campaign impersonated a doctor looking for professional tax services.
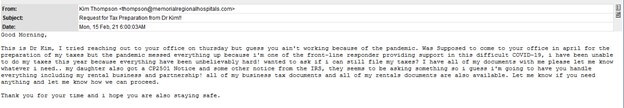
The broken grammar, unusual punctuation and inconsistent capitalization gave away the email as an illegitimate request. Here’s the message in full:
Good Morning, This is Dr Kim, I tried reaching out to your office on thursday but guess you ain’t working because of the pandemic. Was Supposed to come to your office in april for the preparation of my taxes but the pandemic messed everything up because i’m one of the front-line responder providing support in this difficult COVID-19, i have been unable to do my taxes this year because everything have been unbelievably hard! wanted to ask if i can still file my taxes? I have all of my documents with me please let me know whatever i need.. my daughter also got a CP2501 Notice and some other notice from the IRS, they seems to be asking something so i guess i’m going to have you handle everything including my rental business and partnership! all of my business tax documents and all of my rentals documents are also available. Let me know if you need anything and let me know how we can proceed. Thank you for your time and i hope you are also staying safe.
To add a sense of legitimacy to their attack, the nefarious individuals went so far as to register a hospital-related domain to be used in their campaign.
Domain Name: MEMORIALREGIONALHOSPITALS.COM
Registry Domain ID: 2575899170_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.fastdomain.com
Registrar URL: http://www.fastdomain.com
Updated Date: 2020-12-02T01:30:00Z
Creation Date: 2020-12-02T01:30:00Z
Ultimately, the email acted as a lure. Its purpose was to trick a recipient CPA firm into engaging the senders. In the event that a CPA firm responded, the attackers sent along a remote access trojan for the purpose of stealing sensitive personal and financial data as well as using it for whatever purposes they saw fit. That included conducting identity theft, posting it for sale and filing fraudulent tax returns.
A Deeper Dive into the Responsible Threat Actor
It’s not unusual for digital attackers to target CPA firms. As an example, during the 2018 tax season, Zix | AppRiver spotted a campaign that used vague emails to deliver an infected .ZIP archive. That resource ultimately leveraged Java-based infection in an attempt to infect a CPA firm with an Adwind RAT payload.
But the campaign described above was unique in that it came from a familiar threat actor.
“We have observed several CPA firms (our clients) being targeted by this specific threat actor/actors,” explained Gill. “It looks an awful lot like similar attacks we were seeing last year. We believe it to be the same group.”
Indeed, Zix | AppRiver first came into contact with the threat actor in 2020 when the attacker sent out an email asking a recipient CPA firm if they were accepting new clients and how much they were charging for individual returns.
The security firm lured in the attacker by creating a convincing CPA firm domain, setting up a CPA-related website as cover and replying to the initial inquiry. In response, the malicious actors sent over a malicious link purporting to be 2018 tax return documents. That link redirected to melainepitmanestates[.]com, a new site which contained the file “2018_PitMan_USTax.doc.”
This document arrived with an embedded PowerShell script that pulled down an executable file from the new website and used Invoke-Item cmdlet to run it. That executable file turned out to be Netwire, a remote access tool which enabled the threat actor to exfiltrate information from a targeted CPA firm.
Not the First Tax-Related Scam to Make News This Year
The attack described above wasn’t the first tax-related scam that grabbed our attention this year. Some others piqued our interest after other firms and entities reported them to the public.
For instance, on February 10, the Internal Revenue Service warned tax professionals that digital fraudsters were impersonating the government agency in a new scam email campaign.
The emails said that they had originated from “IRS Tax E-Filing,” and they arrived with the subject line “Verifying your EFIN before e-filing.” Their purpose was to steal Electronic Filing Identification Numbers (EFINs) so that attackers could file fraudulent tax returns.
It was just a few days later when Sophos revealed that they had received their first SMS-based tax scam of the season.
The fraudulent text message informed the recipient that they were entitled to a tax rebate of £278.44. According to the ruse, all they needed to do was click on a link that appeared to be related to Her Majesty’s Revenue and Customs (HMRC), the ministerial department in the UK Government which is responsible for collecting taxes.
The link redirected the user to a page that might have tricked some users into thinking it was a legitimate UK Government website. It even included a statement about COVID-19 to add a sense of legitimacy. But the website’s domain name and spelling errors gave it away as a phishing landing page designed to steal unsuspecting visitors’ tax-related information.
This isn’t the first time that fraudsters botched an impersonation scam relating to HMRC. Check out this other scam that Zix | AppRiver came across last year.
How to Defend Against Email-Borne Tax-Related Scams
These attacks highlight the need for organizations to defend themselves and their employees against tax-related scams. One of the ways they can do this is by investing in an email security solution that uses attachment sandboxing, message retraction and other techniques to probe incoming messages for indicators of threat behavior. This tool should conduct this analysis in real time while allowing legitimate correspondence to reach their intended destination.
