Trump Health Scare Used as Malware Lure
Blog
Threat Alert
Trump Health Scare Used as Malware Lure
David Pickett
Trump Health Scare Used as Malware Lure
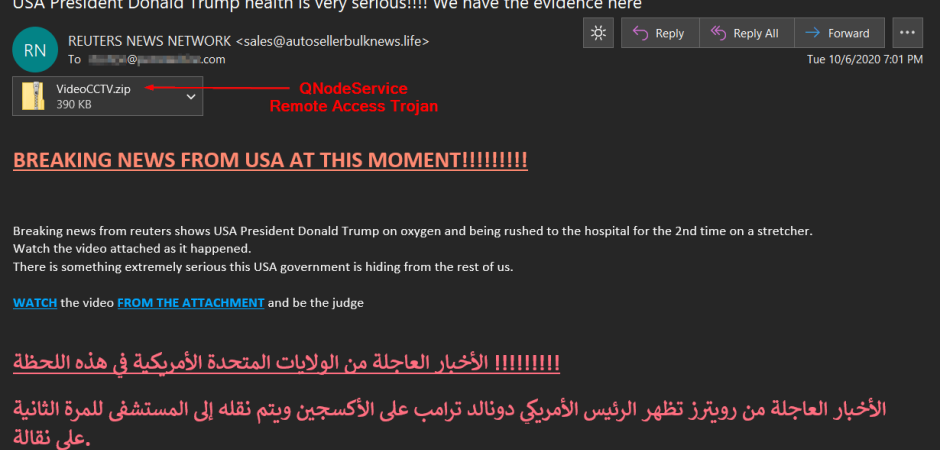
United States election-themed attacks continue to ramp up as we inch toward the close of voting on November 3. On Tuesday, October 6, Appriver/Zix advanced threat protection filters began capturing an interesting malware attack purporting to originate from Reuters News Network with the subject, “USA President Donald Trump health is very serious!!!! We have the evidence here.”
Out of the typical norm, the message body contained similar text in both English & Arabic versions inside the same email. It claimed, “Breaking news from Reuters shows USA President Donald Trump on oxygen and being rushed to the hospital for the 2nd time on a stretcher. Watch the video attached as it happened. There is something extremely serious this USA government is hiding from the rest of us. WATCH the video FROM THE ATTACHMENT and be the judge.”
QNodeService Remote Access Trojan Payload
The attachment to this message (VideoCCTV.zip) contained the QNodeService remote access trojan within. The code was obfuscated using the Allatori Java Obfuscater in an attempt to protect against reverse engineering. However, a deobfuscator transform for Allatori exists on Github. QNodeService is a newer malware discovered in April and previously utilized in Covid-themed attacks. It is written in Node.js, this is an atypical language for malware most likely utilized to evade anti-virus detection. It's designed to steal credentials from browsers, perform file operations, download/execute additional payloads, and allow attackers to exfiltrate data from the system.
End users should be extremely vigilant as these attacks may be sent unsolicited or originate from a compromised trusted contact. Any suspicious messages should be reported to IT staff and/or the security providers for further analysis. Threat actors inside a compromised account will commonly respond back that a file or link is legitimate when the trusted contact is emailed. Users can also contact the sender directly out of band (not via email) to ensure the received message is legitimate.
Defense-in-depth is the best prevention with robust multi-layered security practices and products - email security, endpoint protection, firewalls, network segmentation, VPN's, multi-factor authentication, automatic updates enabled, etc. These steps help strengthen defense posture against the continuous onslaught of threats.
Indicators of Compromise
Main object VideoCCTV.zip
sha256 ccc9d33299c1e6c358f925183ec60168764b34b2f824fba218ba41c89b5efc85
sha1 42bdf99bde24425de761a6b4313e89cfc7cb8320
md5 7125eea628cb4e5c1fb434438a4078d5
DNS requests
domain piolozxx.ddns.net
Email Message Attributes
From: REUTERS NEWS NETWORK <sales@autosellerbulknews.life>
Country-Path: China >
Sending-IP: 117.50.21.109
Reverse-DNS: autosellerbulknews.life
Return-Path: office.works101@yandex.com
