Phishers Using HTML Attachments to Target Indeed Users
Blog
Threat Alert
Phishers Using HTML Attachments to Target Indeed Users
David Bisson

Digital attackers are using HTML attachments as part of an ongoing phishing campaign to steal Indeed users’ account credentials.
Confirm Your Email Address for a Credential Phish
Near the end of March, the Zix | AppRiver team detected a phishing email that appeared to have originated from Indeed.com.
Those responsible for this campaign used branding stolen from the American worldwide employment website and included a footer containing Indeed’s actual physical address. They even used spoofing techniques to make the email look as though it had come from do-not-reply@indeed.com, one of the company’s official “safe sender” email addresses.
No doubt they did all of this as a means of creating a sense of legitimacy for their attacks and lulling their users into a false sense of security.
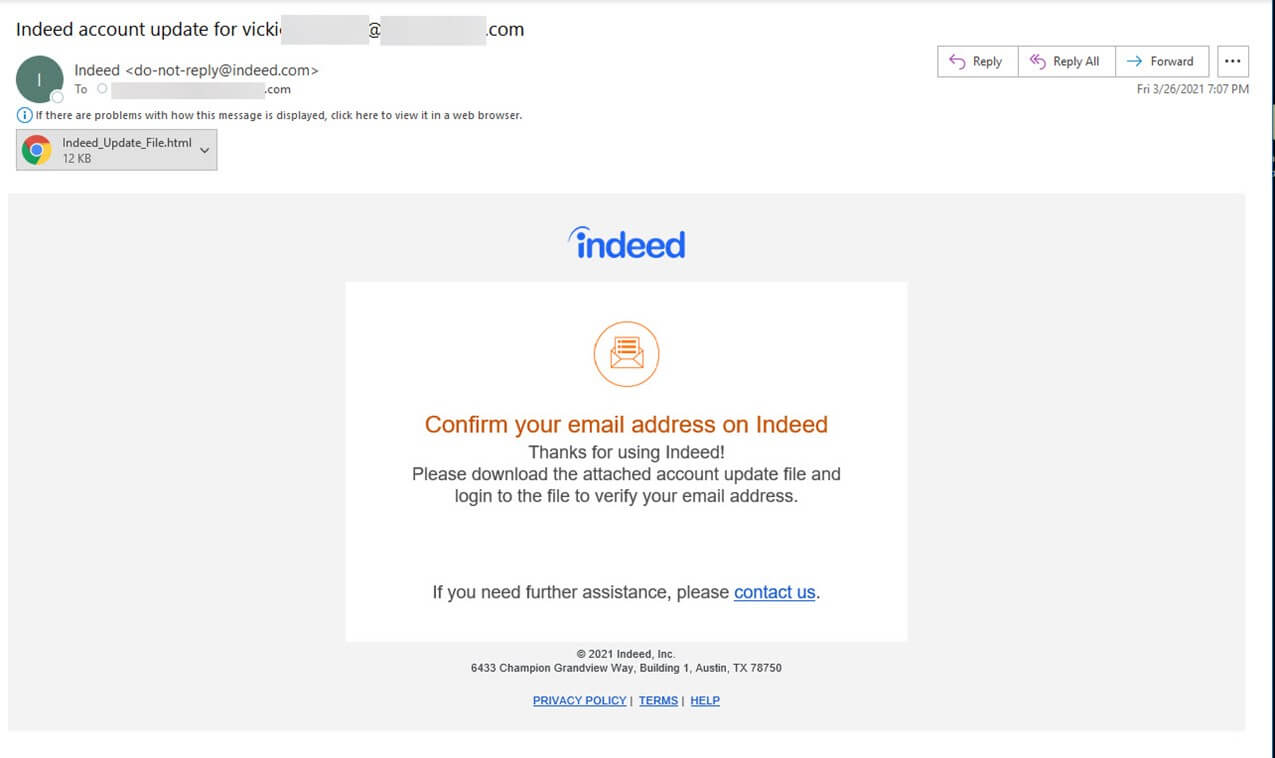
The attack message asked the recipient to confirm their email address on Indeed. (It’s a curious request, as the email arrived with a personalized subject line that already contained the recipient’s email address.)
Here’s where this phishing campaign diverged from other attempts to steal users’ credentials.
The email didn’t ask the recipient to verify their email address by clicking on a link that claimed to log them into their account. Instead, it asked them to open an HTML attachment and use the file to confirm their email address.
Those responsible for this campaign put it this way:
Please download the attached account update file and login to the file to verify your email address.
Legitimate “account update files” aren’t all that common. So, it’s not surprising that the HTML attachment, named “Indeed_Update_File.html,” didn’t do what the attack email said it would. It directed them to a fake login page for Indeed.com instead.
Why the Timing of This Attack Matters
Millions of COVID-19 vaccinations have helped to open up the economy, which is motivating more organizations to begin hiring again. According to CNBC, the jobs report for March 2021 actually exceeded expectations when U.S. organizations collectively added approximately 916,000 people to nonfarm payrolls. The report also revealed that unemployment rate fell to 6%.
As a result, more people could be visiting and using sites like Indeed. They could even be more inclined to click on an embedded link if Indeed appears to have reached out to them via email, perhaps with a potential job opportunity.
It’s a problem for all Indeed users, but the level of risk is heightened for those victims who previously uploaded their resumes to Indeed. Malicious actors can use that information to steal their victims’ identities and then conduct fraud by opening new lines of credit or applying for a new banking account. Those secondary attacks become even easier if their victims used their Indeed credentials across multiple web accounts, thus allowing for password reuse attacks.
But the nefarious activity doesn’t just involve the victims. On the contrary, those responsible for this attack could potentially leverage their victims’ resume information along with their compromised Indeed accounts to try to target employers with other malicious campaigns.
How to Defend Against an Indeed Phish
The campaign discussed above highlights the need for organizations to defend themselves and their users against an Indeed-themed phishing attack. One of the ways they can do that is by investing in an email security solution that’s capable of scanning incoming email messages for malware signatures, suspicious IP addresses, campaign patterns and other threat indicators. This solution should perform its analysis in real time so that legitimate business correspondence can reach its intended destination.
