Email Attackers Using Fake USPS Notifications to Distribute Quasar RAT
Blog
Threat Alert
Email Attackers Using Fake USPS Notifications to Distribute Quasar RAT
David Bisson

Email attackers are sending out fake package notifications from the United States Postal Service (USPS) in an attempt to distribute the Quasar RAT.
A *Different* Package Will Arrive Today, and It’s NOT from the USPS
In the middle of December, Zix | AppRiver flagged an attack email that claimed to originate from the USPS.
The message informed the recipient that their package was in transit to the next USPS facility and that it would arrive later that day.
It then provided the recipient with a linked tracking number, “953865786810209181864,” along with embedded buttons for viewing the package’s tracking and delivery options.
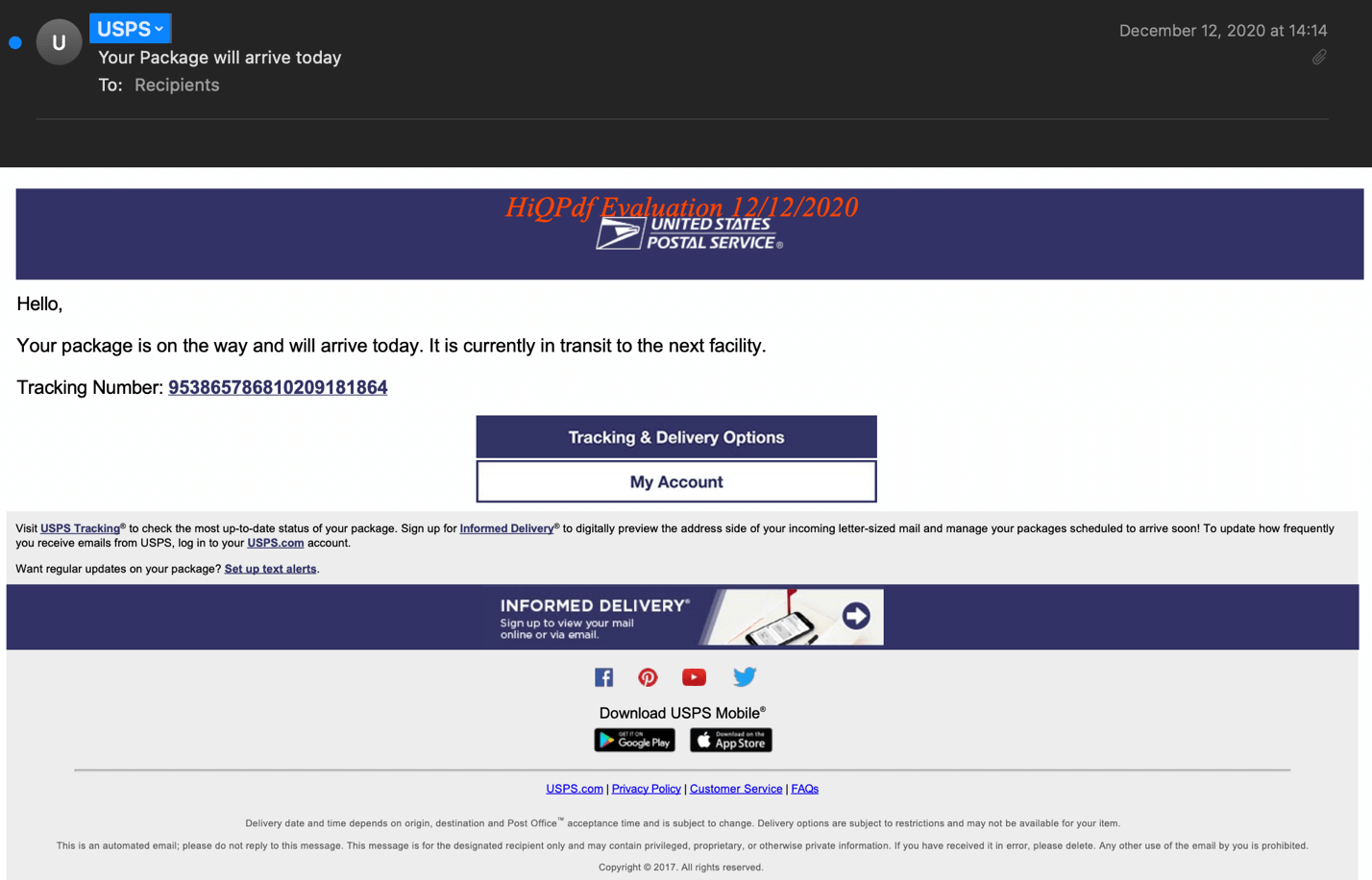
A screenshot of the fake USPS notification. (Source: Zix | AppRiver)
Not surprisingly, there were a few issues with this email.
First, the tracking number included in the attack email didn’t link to a USPS package at the time of writing. A tracking attempt on the USPS website confirmed this to be the case.

A screenshot taken on 12/18/20 of the USPS tracking information for 953865786810209181864.
That’s despite the fact that the tracking number met the format criteria for a legitimate USPS tracking number including a length of 20-22 characters and the absence of letters.
Second, those responsible for the attack campaign used stolen branding and spoofing techniques to try to disguise their email as a legitimate piece of USPS correspondence.
But looking into the sender email address revealed that the message hadn’t originated from a legitimate USPS email account. Indeed, this address appeared to be linked to a carpentry and woodworking company located in Germany.
It’s unclear whether someone had compromised an email account at that company and used it to conduct the email attack described above.
Quasar RAT: A Look Back at the Campaign’s Malware Payload
Clicking on the linked tracking number and/or the “Tracking & Delivery Options” button caused the campaign to drop the Quasar RAT on the recipient’s computer.
On December 18, 2018, the Cybersecurity & Infrastructure Security Agency (CISA) published an alert in which it warned that it had observed Advanced Persistent Threat (APT) actors using Quasar, a legitimate open-source remote administration tool (RAT), to exploit targets’ networks.
Malicious actors seized upon Quasar for additional nefarious activities in the years that followed. In May 2019, for instance, ThreatPost reported that the Chinese-speaking digital espionage group APT10 had begun using two new malware loader variants. Both of those versions dropped a legitimate JVM-based implementation of a JavaScript engine (jjs.exe), driving the attack chain forward to drop PlugX and Quasar as its final payloads.
It was just a few months later when Bleeping Computer covered a phishing campaign that used fake resumes from job seekers to deliver the RAT.
Staying Safe This Holiday Season
This attack campaign highlights the need for organizations and users to protect themselves against malicious emails this holiday season. First, it’s critical that they use security awareness to remain vigilant against scammers who would seek to use packages as lures. COVID-19 and record-breaking snowstorms could cause some delays in the gifts we’ve ordered. For the sake of our digital security, we need to accept the fact that we can’t control everything and that we could leave ourselves exposed by opening package-themed messages in a state of panic.
Second, it’s important that organizations supplement these human defenses with technology. They specifically need a solution that can analyze incoming messages for malware signatures, IP addresses, campaign patterns and other threat indicators. Such a tool should perform this analysis in real-time while allowing legitimate correspondence to reach their intended destination.
