Necurs Botnet Launching Massive Ransomware Attacks
Blog
Thought Leadership
Necurs Botnet Launching Massive Ransomware Attacks
David Pickett
****Update: 12/29/2017 9 A.M.****
Necurs botnet operators continue to show unpredictability. Following the afternoon blog update yesterday they turned up the volume. It ended up being our highest volume day of the year originating from the massive botnet. We blocked 49,784,485 million ransomware messages destined to customers.
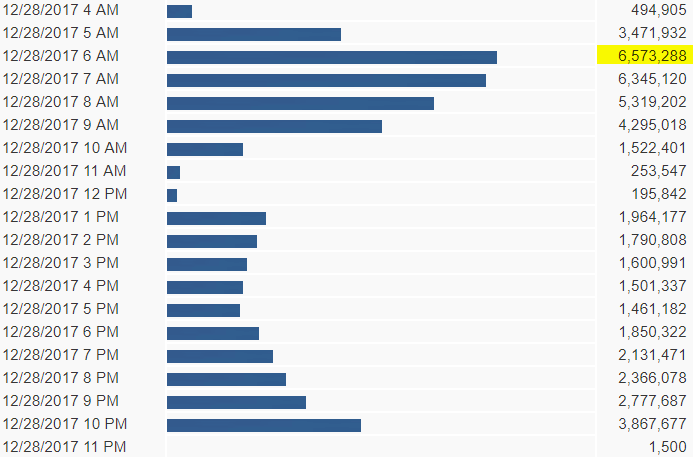
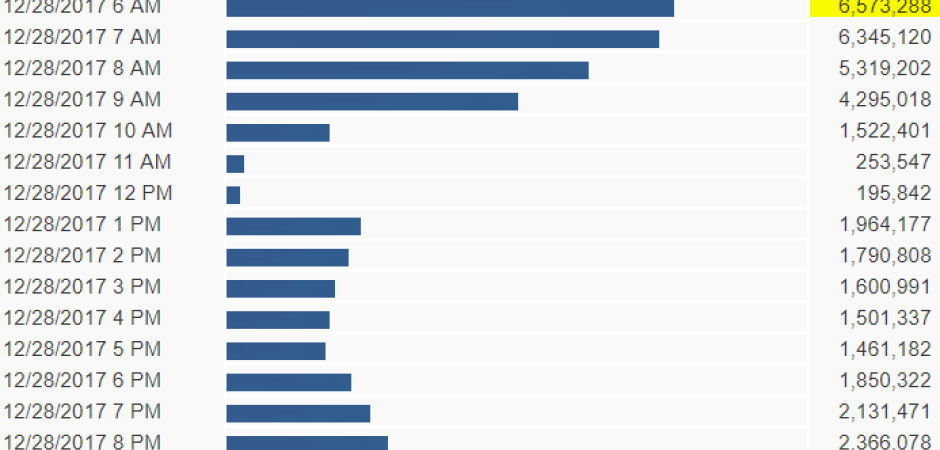
****Update: 12/28/2017 3 P.M.****
Today started out to be the most traffic we've seen by the Necurs botnet this year before it dropped off mid-morning. However, we did log the highest hourly count from Necurs during the 6 a.m. hour. More than 6.5 million messages were stopped in that hour by our filters that were intended to reach our customers.
PREVIOUS BLOG Necurs Botnet Distributing RansomwareIn addition to the typical scam emails we see around the holidays, the Necurs botnet continues to launch massive global ransomware attacks. AppRiver's SecureTide filter has stopped as many as 47 million emails per day - attributed to just the Necurs Botnet - destined for our customers.
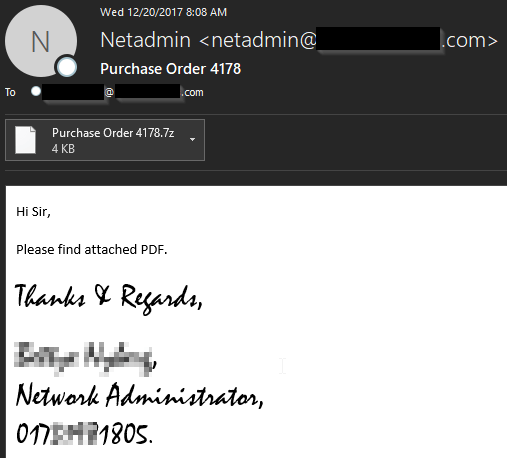
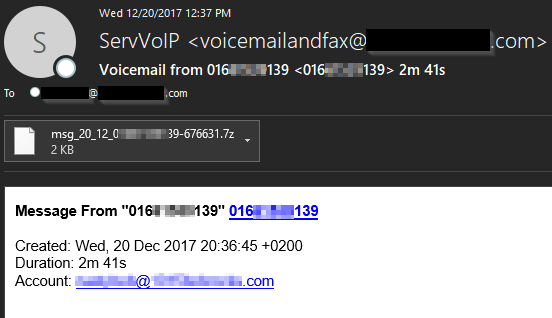
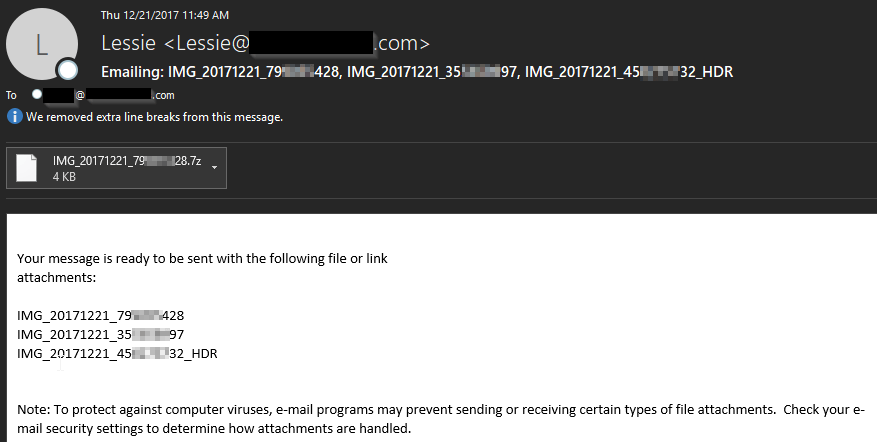
These messages continue to distribute the Locky and GlobeImposter ransomware. Lately the distributors have preferred to use either a malicious .vbs (visual basic script) or .js (javascript) file located inside a .7z (seven-zip archive) to pull down the ransomware payload. The .7z archive helps keep the file sizes small and evade detection for basic email filters that do not scan inside archives.
Necurs Botnet BackgroundThe Necurs botnet is an army comprised of infected user machines. It utilizes a kernel-mode driver to create a backdoor allowing remote access and control of the infected computer. This allows the operators to download malware, hide components from detection, and stop security applications from functioning properly. Necurs is a for-rent botnet and over the years campaigns originating from it vary anywhere from pump-n-dump stock spam, DDoS attacks, to malware created by professional cyber-criminal gangs. It is estimated to control up to 6 million compromised machines with approximately 1-2 million of them active at any given time.
Massive NumbersOn Dec. 19, AppRiver's filters stopped 45,976,814 malicious emails sent by the Necurs botnet. Maximum traffic for it was a just more than 4.6 million emails per hour. These were all .7z that contained malicious .vbs files leading to an infection.
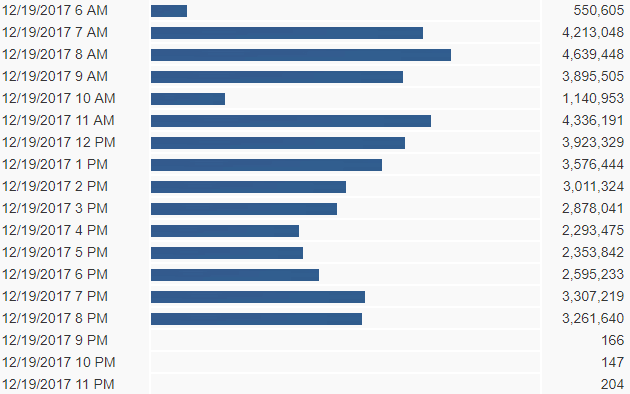 Necurs Botnet Traffic 12/19/17
Necurs Botnet Traffic 12/19/17
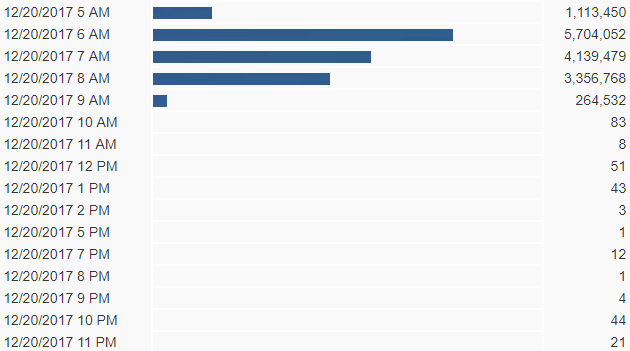
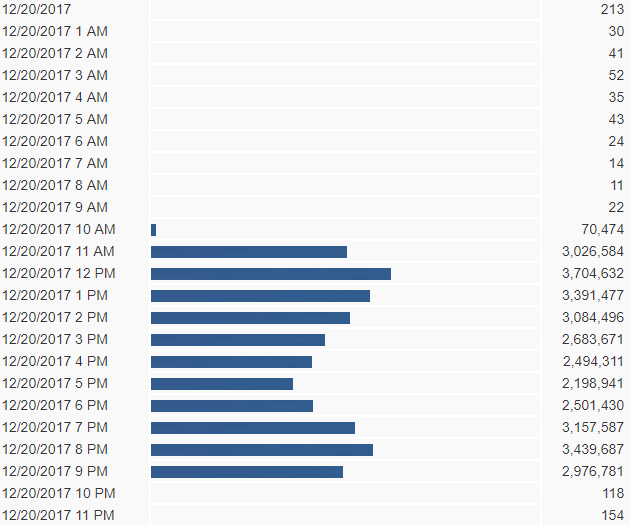
Dec. 20 is the heaviest day we've seen this year (so far) by Necurs with a total of 47,309,380 messages stopped by our filters. Of those, 32,730,828 were the .vbs file, and 14,578,552 were the javascript file inside the .7z archive. Maximum sustained traffic was 5,704,052 million emails blocked during the 6 a.m. hour. Charts below show where they switched from the .js files during the morning back over to .vbs files via an hourly chart.
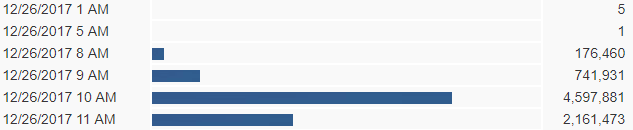
On Dec. 21 and 22, the traffic switched back over to the .js files and began to taper off. We saw 36,290,981 and 29,602,971 messages blocked respectively, for those two days, before the botnet went quiet from Dec. 23-25. Today (Dec. 26), Necurs re-awoke from its slumber for a couple hours then went quiet again.
Hard to say why, however, I would hypothesize the operators may have been testing or monitoring the rate of infections and realized many workers are on vacation. As of the time this blog was authored we've captured the below statistics for today:
Message Examples
Necurs 12/20/17 .JS
Necurs 12/21/17 .JS
ARE YOU CONNECTED?
Are you following AppRiver’s social media? Like us today on Facebook, Twitter, YouTube and LinkedIn.
YOU MIGHT ALSO LIKE
https://blog.appriver.com/2017/10/ransomware-variant-exploits-dde-functionality/