Office 365 Business Email Compromise Attacks Proliferate
Blog
Thought Leadership
Office 365 Business Email Compromise Attacks Proliferate
David Pickett

Office 365 Business Email Compromise Attacks
The Office 365 (O365) platform has experienced tremendous growth and there is no sign of that trend slowing. More businesses than ever reside with - or plan to migrate accounts to - the expanding Microsoft Business or Enterprise services. Scammers have taken notice and have crafted simple, effective social engineering attacks targeted to (and from compromised) O365 users.
Since the last quarter of 2017, we have blocked an abnormal quantity of Business Email Compromise attack campaigns. These are a version of man-in-the-middle attacks exploiting the trust that goes with the victims known contacts. Western African (likely Nigerian) scam groups have improved social engineering techniques, which ultimately lead to credential theft and financial fraud. Our SecureTide Filtering and Phenomenal Care Support teams have documented data for this attack. The information provided below details the tactical phases of ongoing Office 365 Business Email Compromise attacks and credential harvesting by these scammers.
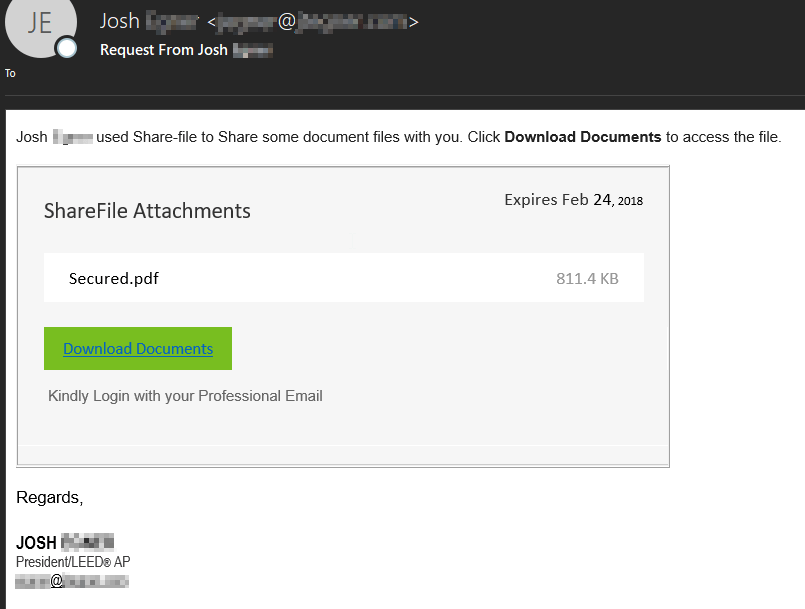
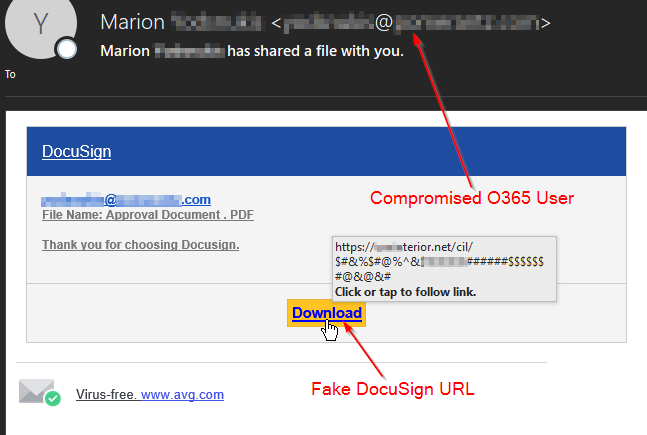
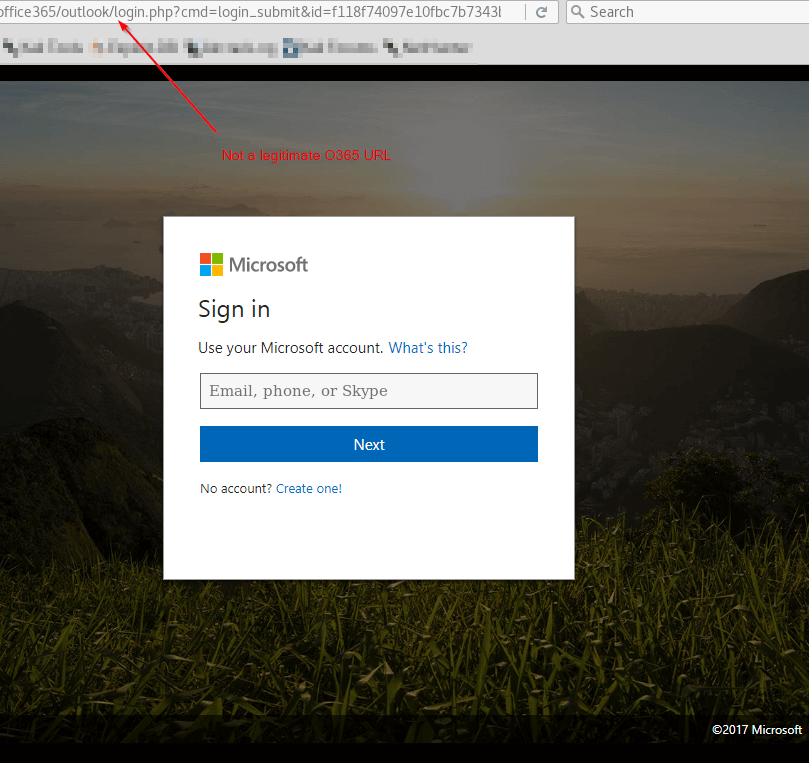
Phase 1: Initial Phishing MessagesAlthough campaigns varied, we investigated the results and identified similar traits among many samples. SecureTide logging showed an abnormal increase of messages from O365 IP addresses quarantined for filtering clients. However, it was clear these malicious messages were sent from compromised O365 users. Links in the messages lead to mainly O365 and DocuSign-themed fake credential-harvesting sites.
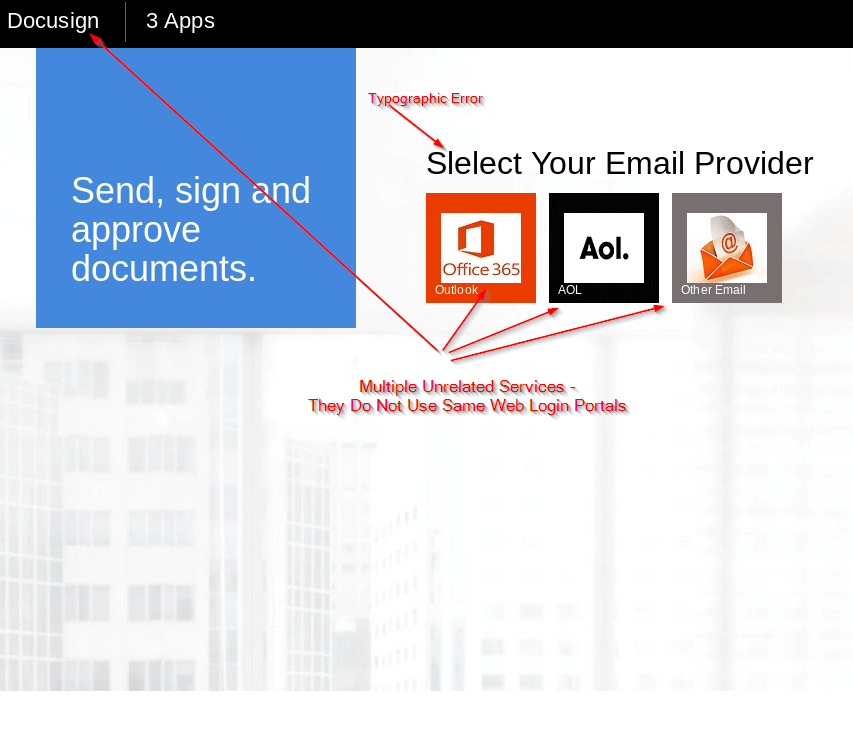
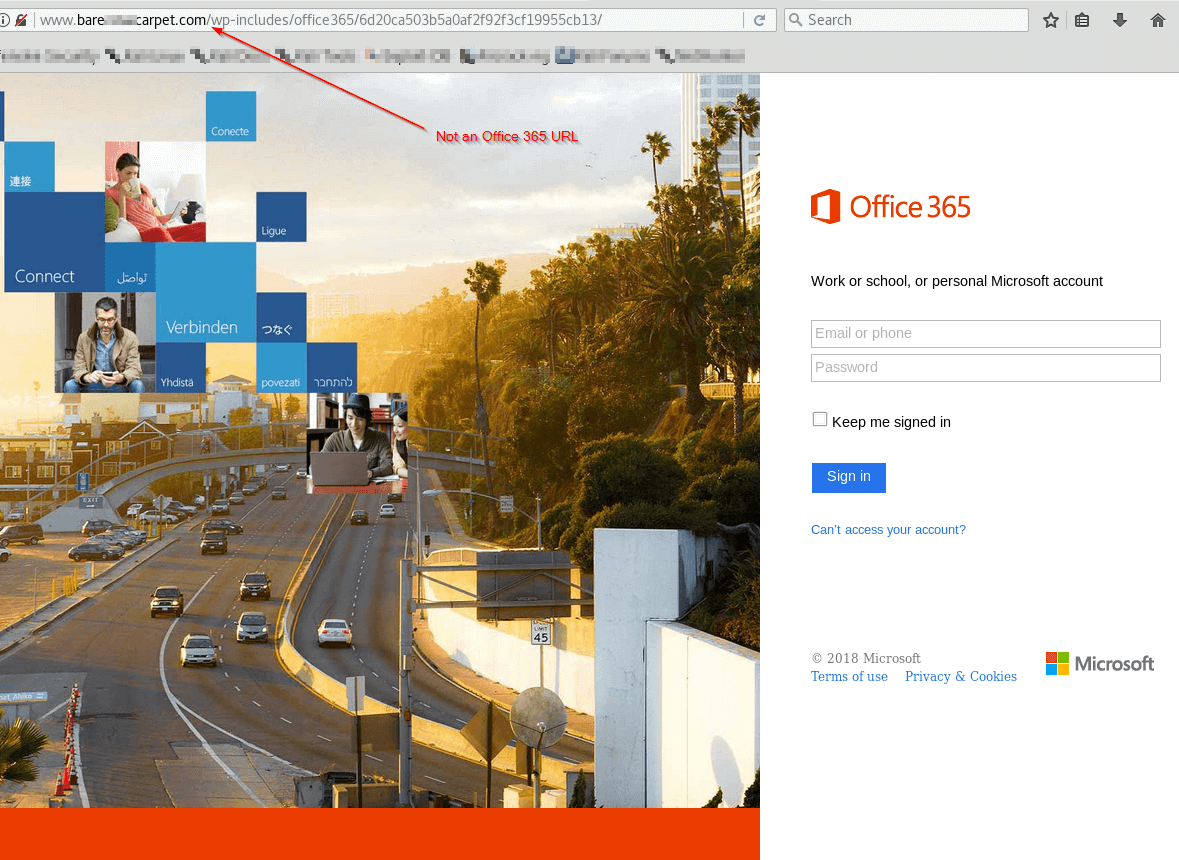
Phase 2: Credential Harvesting Web Portals
It is important users be mindful of suspicious techniques before they become duped by credential harvesting sites. Warning signs include incorrect or misleading urls, formatting mistakes, and typographic or grammatical errors. Many enterprising credential harvesting sites include multiple unrelated services as a sign-in option on one page. These legitimate services do not share user email addresses and credentials, nor maintain a universal sign in site like a couple examples below.
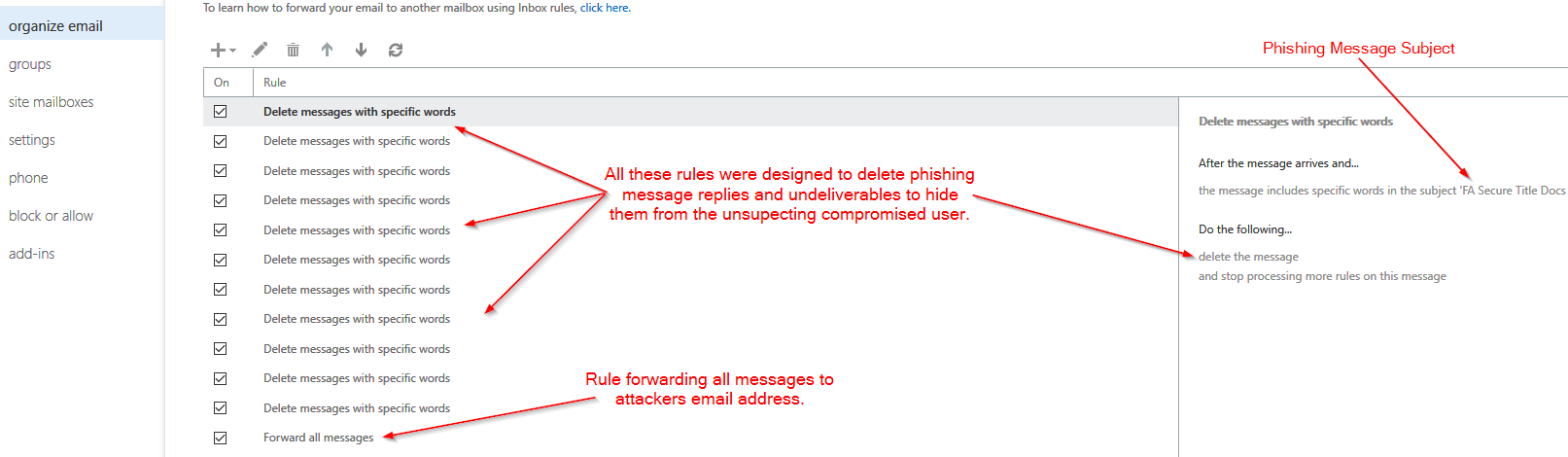
Phase 3: Mail Rules to Establish PersistanceJennifer Rogers, a Support Team Lead, assisted in remediation efforts. She noticed users initially reported not receiving messages to their account. Unbeknownst to the user, attackers had invaded their mailboxes. Mail rules were created to delete messages helping to disguise suspicious activity. They also set rules to forward all messages externally and had connected accounts.
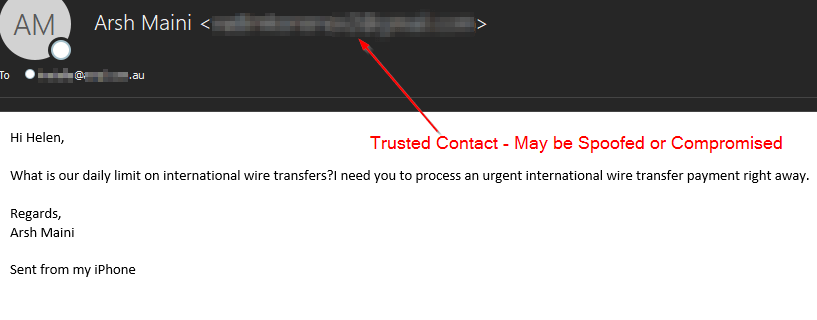
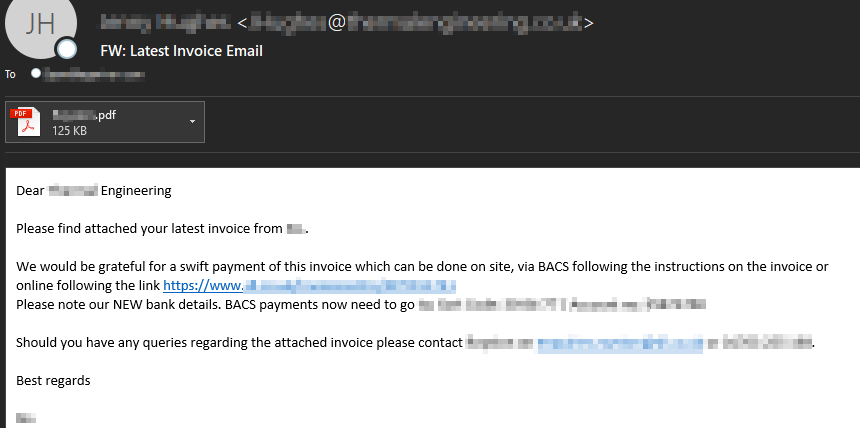
Phase 4: Phishing The Users Contacts In Pursuit of Financial FraudOnce attackers are setup in a victim's mailbox, they go thru the users stored contacts and address books. Many times they would reply to previous conversations. They were ultimately looking to social engineer the finance/billing department or trusting contacts for fraudulent financial transactions. Anyone who might pay wire transfer requests, fraudulent invoices, or billing statements were targets for these Office 365 Business Email Compromise Attacks. Contacts not targeted for financial theft were sent further phishing emails leading to the credential theft portals. Then the process continues all over again beginning at phase one. The scammers end goal is two-fold, stealing credentials and conducting financial fraud.
Tips for Reducing O365 Attack RiskNathan Mitchell, Office 365 Team Lead, offers the following advice for administrators to help reduce the risk of an O365 attack:
"The recent waves of phishing attacks hitting Office 365 users have been alarming to many organizations," Mitchell said. "We highly recommend enabling Multi-Factor Authentication (MFA) in Office 365 to help prevent unauthorized access to Office 365 users"
Mitchell offers these tips for users to consider in conjunction with MFA:
Modify the default O365 filtering policies to make filtering more strict. Office 365 administrators should utilize built in logging and reporting functionality to help monitor the security of user accounts. For advanced reporting, administrators can leverage Azure Active Directory Premium licenses to help detect suspicious and unusual sign-in activity. AppRiver ProtectionThere is no shortage of spam, malware, phishing, or nefarious websites AppRiver's staff and systems continuously protect and defend against. Malicious actors work around the clock to infect your network, and we at AppRiver work even harder to stay one step ahead of them. Our team is here 24/7 365 days a year protecting and supporting clients from Office 365 Business Email Compromise Attacks and other security risks.
We always recommend defense in depth by utilizing layered security solutions. Adding SecureTide email filtering for inbound/outbound email traffic and SecureSurf for web filtering in conjunction with the built-in offerings of O365 or M365 is an example of this. This builds upon the existing security functionality integrated into products and provides a more comprehensive security solution that will greatly enhance protection for users.
{{cta('8dddce58-7c8f-4e35-8895-353c48f9163a')}} CONNECT WITH USLike us today on Facebook, Twitter, YouTube and LinkedIn.
RELATED CONTENThttps://blog.appriver.com/2018/02/attackers-leverage-stolen-credentials-malware-attacks/