Safari Suffering from "Yet to Be Patched" URL Spoofing Flaw
Blog
Thought Leadership
Safari Suffering from "Yet to Be Patched" URL Spoofing Flaw
Fred Touchette

Researcher David Leo of Deusen.co.uk has announced a proof of concept vulnerability that was active , until recently, in both Chrome and Safari browsers that allows attackers to spoof legitimate URLs in their address bar while taking web surfers to a completely different site. Chrome has since patched this vulnerability, but Safari has not. This leaves all devices that rely on the Safari browser vulnerable to this exploit. This includes current Macs running OSX, iPhones and iPads.
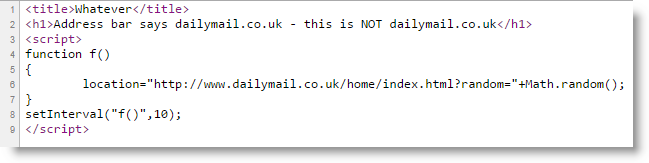
This exploit works by running a quick and tiny code snippet in the browser when a supposed legitimate link is provided to end users. The actual "legitimate link" is requested and the browser begins to head in that direction, however before it can, the exploit redirects the browser to the false destination. The original URL destination remains in the address bar, making it appear as though the user has ended up at the legitimate site. The code is very simple and very light weight making it possibly very enticing to those who would like to offer up a very convincing phishing attack. Through spoofing, attackers already utilize legitimate sites and news stories to make their attacks more convincing, usually by stealing graphics and headlines. A couple of safety precautions, or things to look out for in these attacks, would be to mouseover the link provided to make sure it was pointing where it says it is pointed. Otherwise ending up at a destination that was not advertised is another bright red flag. However in this style of attack, everything would simply appear normal and correct on the surface.
This is a look at the code that executes this exploit:
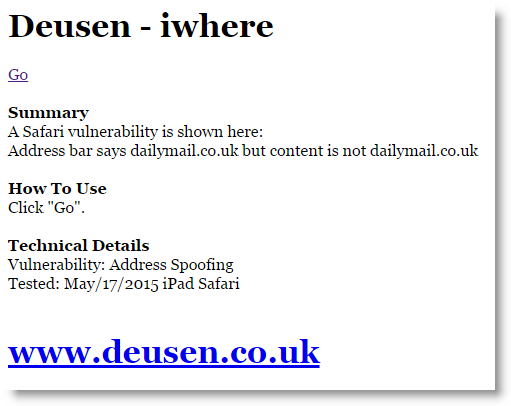
This particular PoC attack makes the user believe they are headed to the news site dailymail.co.uk, however the hidden redirect takes viewers back to the research page on deusen.co,uk while maintaining dailymail.co.uk in the address bar.
To test this exploit out on your system, David Leo has provided a test page to see if you are a potential victim located here: http://www.deusen.co.uk/items/iwhere.9500182225526788/ SImply gress "Go" and if Dailymail shows in your address bar, you are still vulnerable to this attack and are encouraged to be extra careful while browsing the internet or following links within emails from unexpected sources.