Microsoft Azure Customized Domain Name Phishing Attacks - Compromised Users and Geolocation Data Exposed
Blog
Thought Leadership
Microsoft Azure Customized Domain Name Phishing Attacks - Compromised Users and Geolocation Data Exposed
David Pickett

THREAT ALERT UPDATE: Cybercrooks Abusing Azure Custom Domain Name Feature
On Sept. 7, 2018, we detailed how malicious attackers abuse Microsoft Azure's Custom Domain Name registrations to host credential phishing sites.
This type of "living-off-the-land" attack utilizes phishing sites which reside on Microsoft's web servers. The phishing emails are also frequently sent from Microsoft's servers. Attackers are currently using: .web.core.windows.net, .blob.core.windows.net, and .azurewebsites.net for these customized Azure domain name attacks.
While researching the latest variants, we discovered some interesting finds that warrant an update to our previous threat alert. The first find was a successful attack where 284 different user credentials and geolocation information was exposed to the internet.
The second find was inevitable and anticipated - attackers began embedding these malicious links in attachments, which AppRiver's email security filters are capturing.
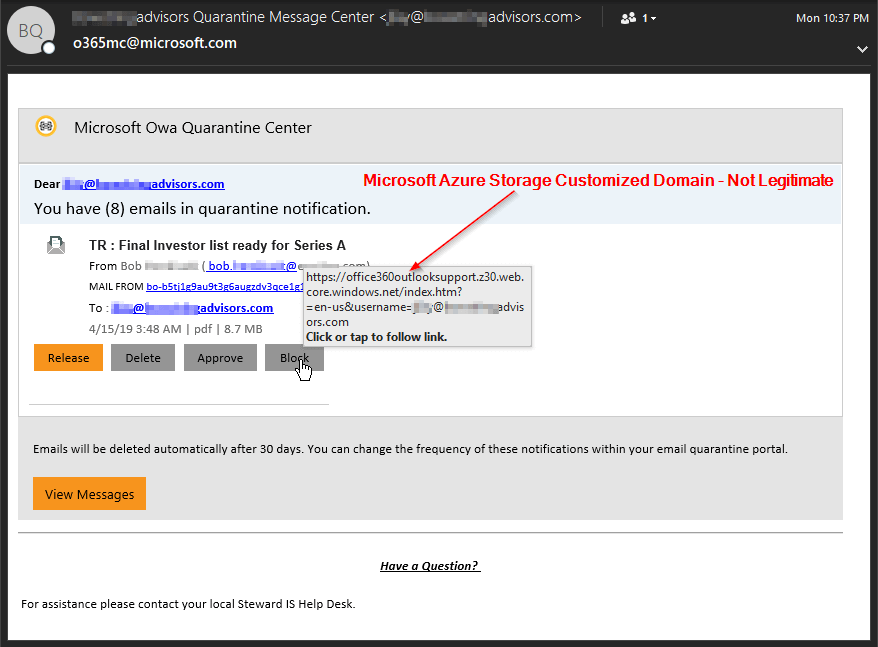
Compromised User Data Exposed
For this particular attack, the malicious actor registered office360outlooksupport as their Azure storage custom sub-domain to exploit unsuspecting users.
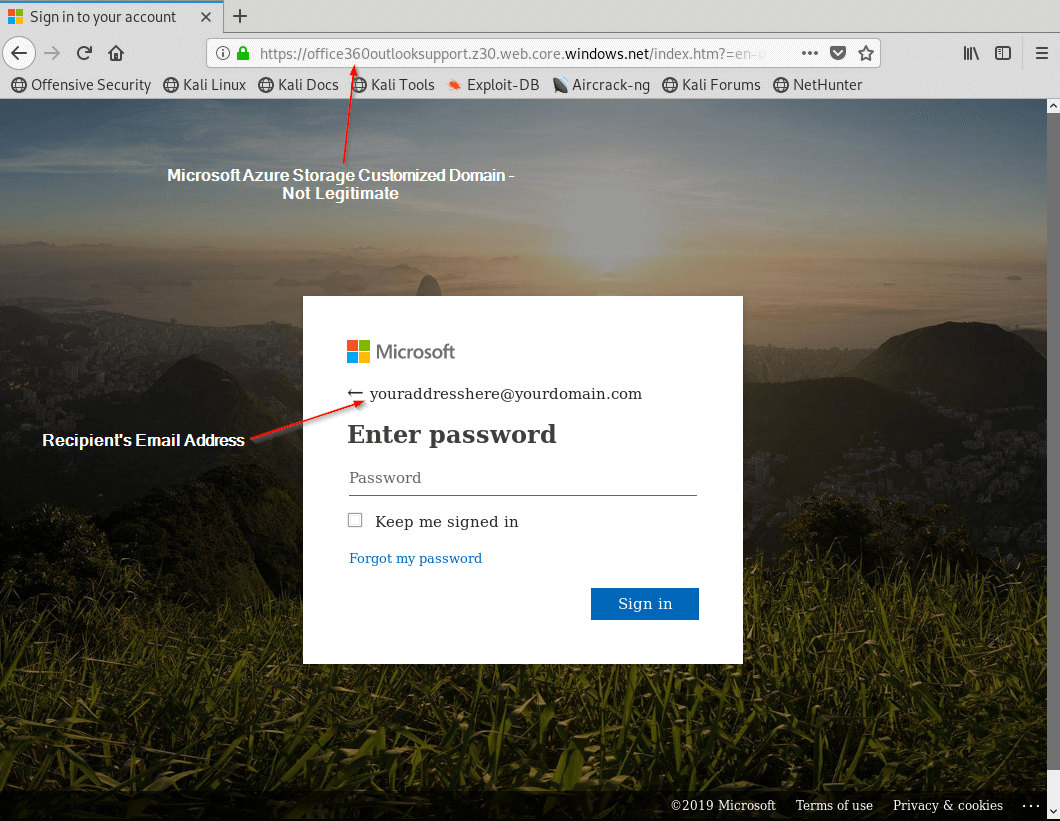
Following the link to the phishing site yields the all-to-familiar clone of the Microsoft login portal. It automatically pre-fills the recipient's address by using the address inserted into the phishing email they received.
Compromised User Data Exposed
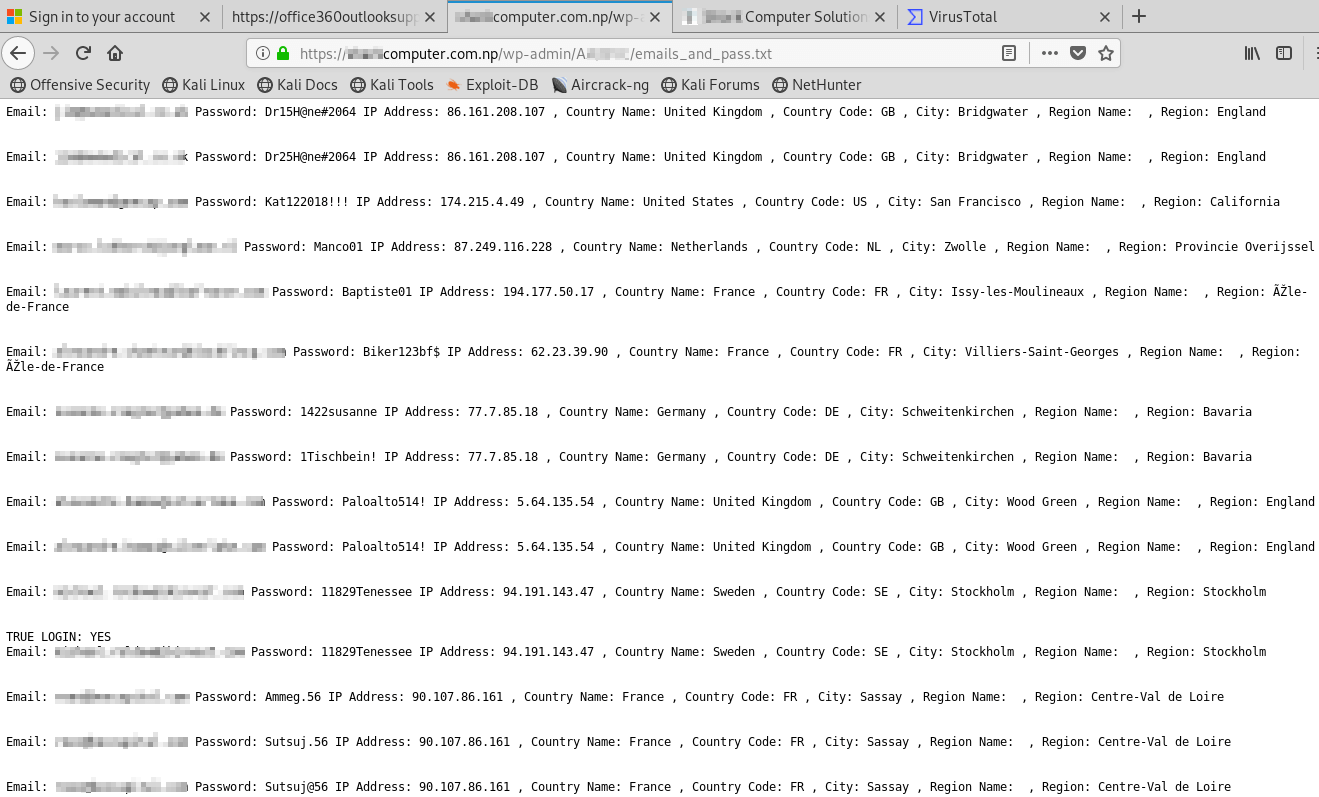
Viewing the source code of the phishing portal above, we were able to see the attacker was posting the stolen data to an external compromised site. Ironically, the compromised site where the credentials were being sent was a website design company located in Kathmandu, Nepal, who had no idea this was occurring. Upon navigating to the site, we found the attacker had left an open directory. This allowed us to navigate thru the site structure and we noticed a file named, "emails_and_pass.txt."
Inside the emails_and_pass.txt file were 284 compromised users who had attempted to login to the phishing portal along with their geolocation data. While the attacker went thru the effort of crafting the phishing emails and site, they had left the stolen credentials open for anyone to see. Many of these users had attempted to login multiple times using different passwords. By doing this, attackers also have visibility into how these users have changed their passwords over time. This opens the possibility to additional password attacks directed toward those users.
Azure Customized Domain Phishing Links Now Inside Attachments
Since our previous threat alert, malicious actors also have begun to insert these Azure phishing links into Word and PDF attachments as well.
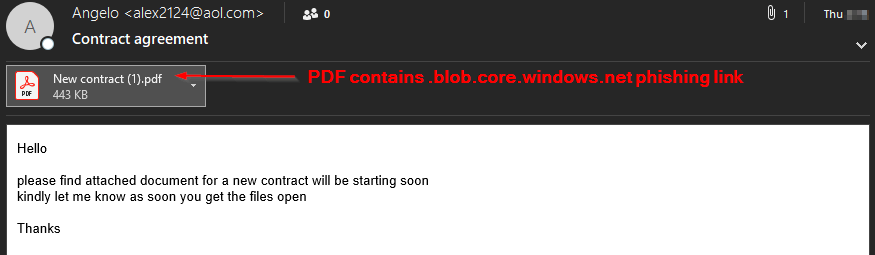
Viewing the attached PDF below - this example was converted from Word document to PDF using a popular online converter. This makes it simple for an attacker to create weaponized pdfs without having to purchase pdf creation software.

AppRiver Tips
Always check the 365 login portal url you are using and only sign in to https://portal.office.com or https://login.microsoftonline.com. Add company branding to help reduce the risk of a user logging into a phishing site. Setup multi-factor authentication for 365 users. In the event the credentials are compromised, this lessens the risk of the attacker being able to use them for malicious purposes. Leverage the Microsoft Secure Score to assist in improving security posture.
AppRiver Protection
There is no shortage of malware, phishing, spam, or malicious websites AppRiver’s staff and systems continuously protect and defend against. Malicious actors work around the clock, therefore, we at AppRiver work even harder to stay one step ahead. Our team is here 24/7 365 days a year protecting and supporting clients and partners from security threats.
